The Authentication Dilemma: Rising Vulnerabilities and Reluctance to Patch in OT

In today's digital age, the importance of robust cybersecurity cannot be overstated. Yet, despite the growing number of authentication vulnerabilities, many organizations remain hesitant to implement necessary patches and continue to exhibit poor password hygiene. This reluctance to address fundamental security flaws leaves critical systems exposed to potential attacks. In this article, we delve into the rise of authentication vulnerabilities, examine the underlying reasons behind the resistance to patching, and discuss the impact of poor password practices on overall cybersecurity. Through a closer look at these issues, we aim to highlight the urgent need for a cultural shift towards better security practices and the adoption of more rigorous authentication measures.
Why Are Customers Reluctant to Patch and Change Passwords?
Customers often hesitate to patch and change passwords for several reasons:
- Complexity and Time Consumption: Patching systems can be time-consuming and complex, especially for large organizations with numerous devices and users.
- Downtime Concerns: Applying patches might require system reboots or downtime, which can disrupt business operations and lead to productivity losses.
- Compatibility Issues: Some patches may not be compatible with existing systems or software, leading to potential functionality issues or bugs.
- User Resistance: Employees may resist changing passwords frequently due to the inconvenience of remembering new passwords or the frustration of dealing with complex password requirements.
- Lack of Awareness: Some organizations may not fully understand the importance of regular patching and strong password practices, leading to complacency.
- Resource Constraints: Limited IT resources and budget constraints can make it challenging for organizations to keep up with the latest patches and enforce strong password policies.
- Legacy Systems: Older systems may not support the latest security updates or password policies, making it difficult to implement changes without significant upgrades or replacements.
- Fear of Lockouts: Frequent password changes can lead to users being locked out of their accounts, especially if they forget their new passwords or if the authentication process is too stringent.
These factors contribute to a reluctance to adopt best practices in cybersecurity, leaving systems vulnerable to attacks. Addressing these concerns through education, streamlined processes, and user-friendly solutions can help improve security measures.
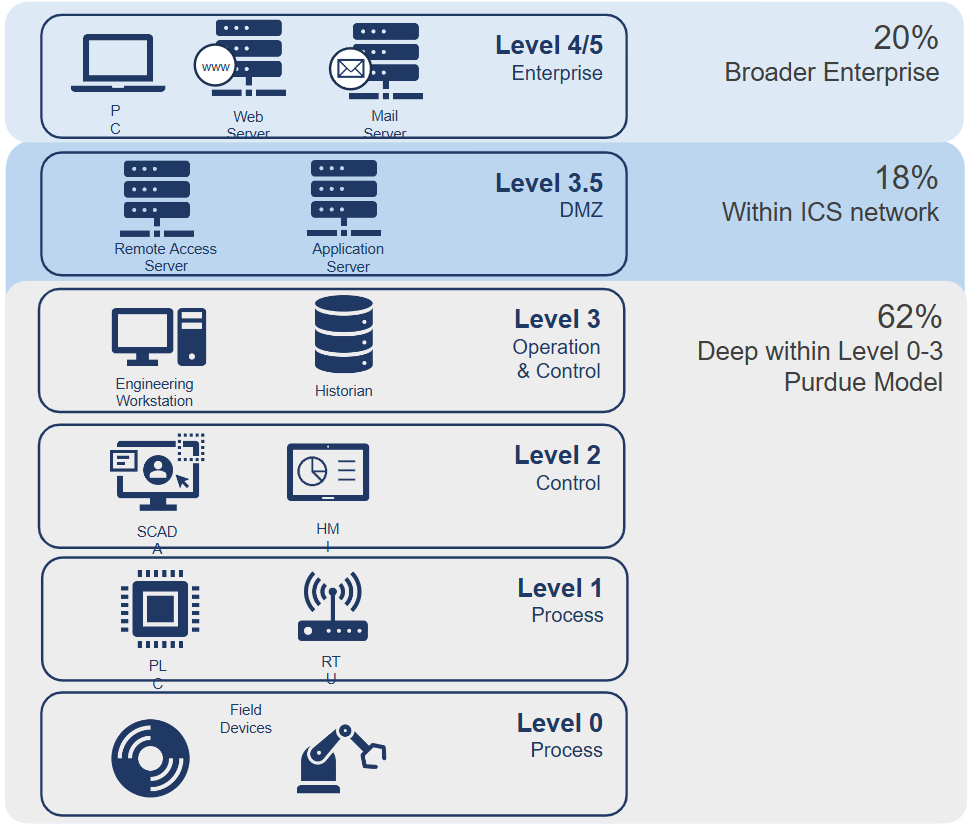
Where do most vulnerabilities exist?
In the Purdue Model for ICS security, most vulnerabilities tend to exist in Level 2 and Level 3. These levels are particularly attractive to cybercriminals because they provide access points into ICS networks.
- Level 2: This level includes the control systems that directly manage the industrial processes. Vulnerabilities here can disrupt operations and compromise process integrity.
- Level 3: This level involves the supervisory control systems that monitor and control the lower levels. Exploits at this level can give attackers deeper access to the network, potentially allowing them to manipulate critical systems.
Most Recent Authentication Vulnerabilities
- CVE-2024-41798 is a critical vulnerability identified in Siemens SENTRON 7KM PAC3200 devices. The vulnerability arises from the devices only providing a 4-digit PIN to protect against administrative access via the Modbus TCP interface. Attackers with access to the Modbus TCP interface can easily bypass this protection through brute-force attacks or by intercepting the clear text communication. The severity of this vulnerability is reflected in its CVSS score of 9.8, indicating a high level of risk. Siemens has acknowledged the issue and provided guidance on mitigating the risk.
- CVE-2024-45274 is a critical vulnerability affecting MBConnectLine Mbnet.mini and Helmholz Rex 100 devices. The vulnerability allows an unauthenticated remote attacker to execute OS commands via UDP on the device due to missing authentication. This means an attacker can gain control over the device and potentially disrupt operations, leading to high risks to confidentiality, integrity, and availability. The vulnerability has a CVSS score of 9.8, indicating its severity. It's crucial for affected organizations to apply the necessary patches or updates provided by the vendors to mitigate this risk.
- CVE-2023-2060 is a critical vulnerability affecting Mitsubishi Electric's MELSEC iQ-R Series and iQ-F Series EtherNet/IP modules. The vulnerability stems from weak password requirements in the FTP function, allowing a remote, unauthenticated attacker to access the module via FTP by performing a dictionary attack or password sniffing. This vulnerability has a CVSS score of 8.7, indicating its severity.
- CVE-2024-10386 is an authentication vulnerability affecting certain Rockwell Automation products. The vulnerability could allow a threat actor with network access to send crafted messages to the device, potentially resulting in database manipulation. This vulnerability has a CVSS score of 9.3, indicating its critical severity.
How can swIDch help?
swIDch's OTAC (One-Time Authentication Code) technology eliminates the need for passwords, addressing numerous security concerns tied to traditional authentication methods. By removing passwords, it mitigates risks associated with weak or reused passwords, which are common entry points for cyberattacks. OTAC generates dynamic, one-time codes for each login, making it extremely difficult for attackers to gain unauthorized access through credential theft or brute-force attacks.

This robust authentication method simplifies security management, reduces the burden of frequent password changes, and minimizes the potential for human error. As a result, organizations can significantly enhance their security posture, ensuring that only authorized users can access critical systems without compromising usability or efficiency. By adopting OTAC, businesses can overcome the limitations of password-based authentication and protect their digital assets more effectively.
--------------------

Author: Vinny Sagar, Solution Architect, swIDch
With over 15 years of experience in pre-sales, consulting and software development in the Identity and Cyber Security space Vinny has helped many clients across various industries and regions to design and deploy Zero Trust solutions that meet their specific needs and challenges.
--------------------

swIDch will continue its quest to innovate and pioneer next-generation authentication solutions. To stay up-to-date with the latest trends sign up to our newsletter and check out our latest solutions.

Approval has long been treated as a proxy for control. If access is approved, it is assumed to be safe. If the request

At a large industrial site, a contractor needed temporary access to a controller to complete routine maintenance. The

At a large manufacturing plant in Northern Europe, a routine maintenance task nearly became a shutdown. An external
Looking to stay up-to-date with our latest news?