.png)

Identity & Access Management OTAC
Manage your digital identities and control user access
to critical corporate information alongside a super-secure
single-step user authentication process for both
on-premise and work-from-home environments
Pain points
The business environment is changing rapidly, causing many companies to modify their work environment and procedures. With remote work and the use of personal mobile devices as access cards, obtaining and sharing information has become easier than ever. At the same time, however, this opens up businesses to significant risks.

RF cards at risk of loss, theft, and duplication
A total of 90% of the access control market is dominated by RF cards that
communicate on frequency. However, because of the risk of duplication and
loss, its security is questionable.
ID/PW theft because
of weak remote work /
network separation environment
Because of the COVID-19 crisis, remote workers became susceptible to social engineering methods. In particular, 91.5% of related cyber threats are from email phishing. The use of a VPN to provide end-to-end encryption is often recommended to counteract such threats, but using a VPN without additional authentication steps can expose the authentication to theft.
Information centralized
to smartphones
Personal ID and payments are all available on smartphones adding to an ever increasing reliance on devices. Nonetheless, areas such public offices, military bases, power plants, etc. often ban devices before entry meaning devices cannot always be relied upon for access. Devices are also susceptible to technical malfunctions and battery limitations. To this extent smartphones/devices act as the single point of failure (SPOF); if it fails or is hacked, the entire network is at risk.
The solution
swIDch’s OTAC provides you control over users in mobile and remote work environments or grants a certain level of authority to access your corporate resources and networks. It also offers more efficient control by providing a safe and simple authentication process when physical access to a certain space is required. OTAC can be provided both as software and hardware to upgrade individual or corporate access management.
> Read our Indonesia E-Stamp case study here
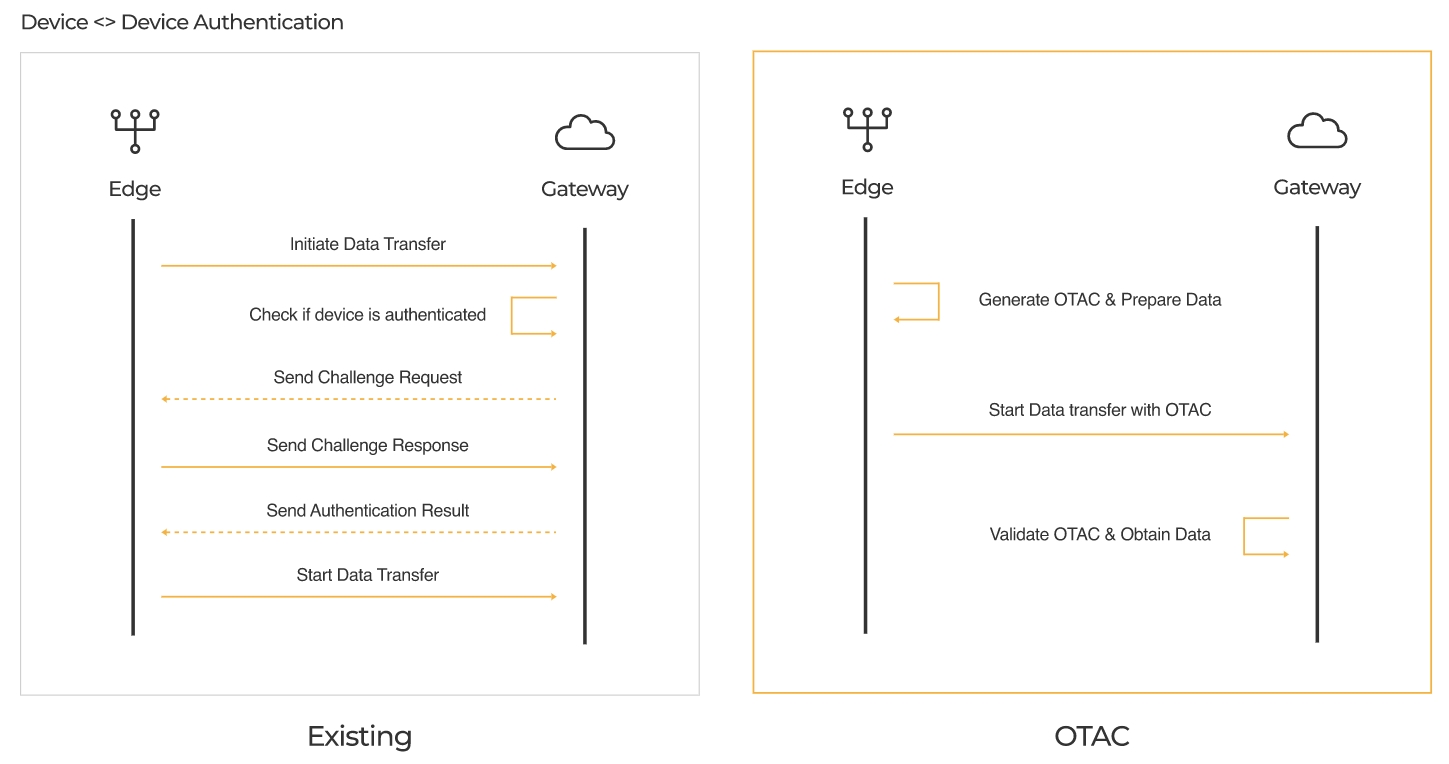
OTAC for Identity & Access Management
OTAC is a revolutionary authentication technology enabling enterprises to secure and protect data and people. Users can generate dynamic one-time access codes from their own mobile devices in an off-the-network environment with which users can access corporate resources and networks. OTAC can also be easily integrated with the existing IAM solution and the user experience is never compromised.


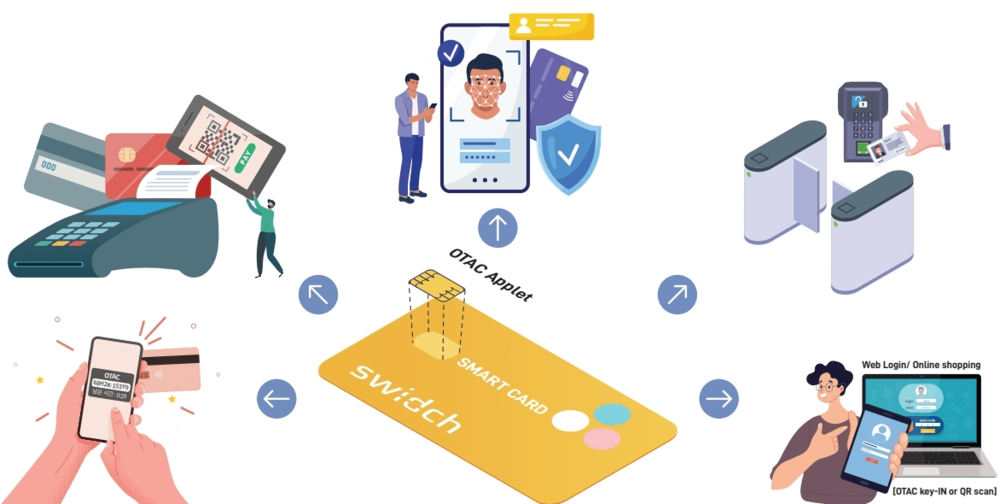
OTAC for integrated management including access/payment/ID
Enterprises issue and manage at least 3.5 cards per each employee for payment, identification, and access purposes such as employee ID card, corporate credit/debit card, and corporate OTP for online payment. As a result, people tend to rely on their smartphone for integrated functions. This results in over-reliance on a single device; battery limitations, restricted area access and closed network environments can be problematic. With OTAC embedded-IC Chip (dual interface chip, NFC supported) card and minimal use of smartphones or access devices, many of the above-mentioned issues can be resolved. Your employees can enjoy diverse functions including payment, access management, system login, and identity authentication (KYC), all on a single physical card.
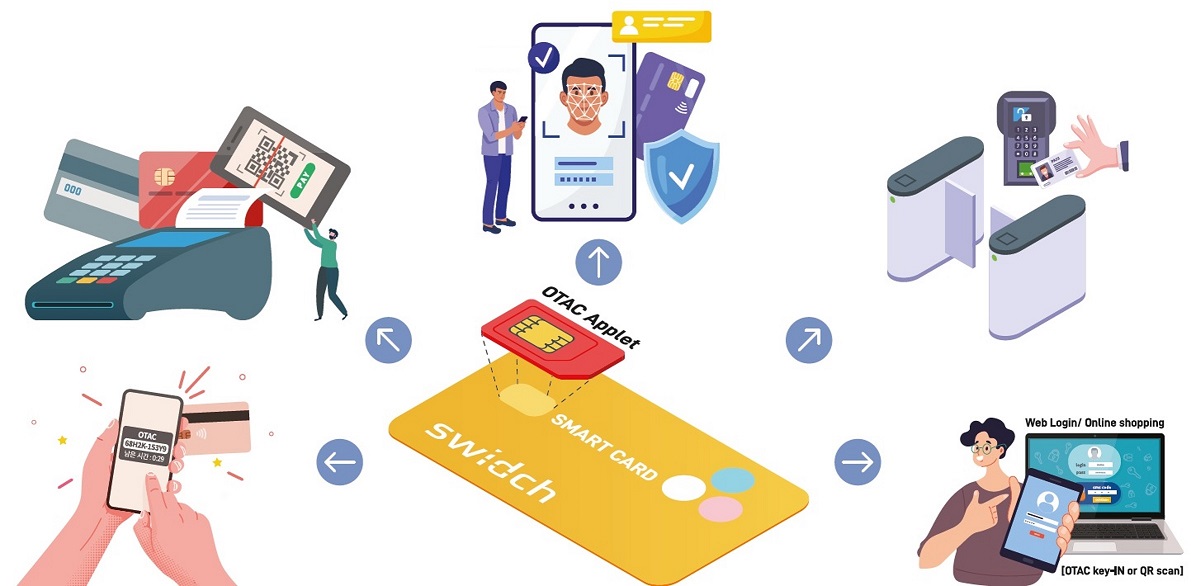

- IC card type: Combi card (ISO 7816)
- OTAC code generation through NFC card tapping (mobile phone and access gate)
- Various functions from gate/door access to system login and OTP function
- Expandable to payment card through partnership with finance service firms
- Fingerprint sensor and display option available
- System log in and gate/door access control all available

- Using energy-harvesting technology (No Battery)
- OTAC code generation through fingerprint recognition
- Can utilize non-network environment
- E-ink Display option available (QR Code applicable)
- System log in and gate/door access control all available
.png)
- OTAC log in code generation through card tapping,
bio-authentication on mobile device, etc. - Using fingerprint recognition or ID card
- Using mobile-generated code or QR code
- Can utilize non-network environment
- Additional functions can be linked (App functions)
- System log in and gate/door access control all available
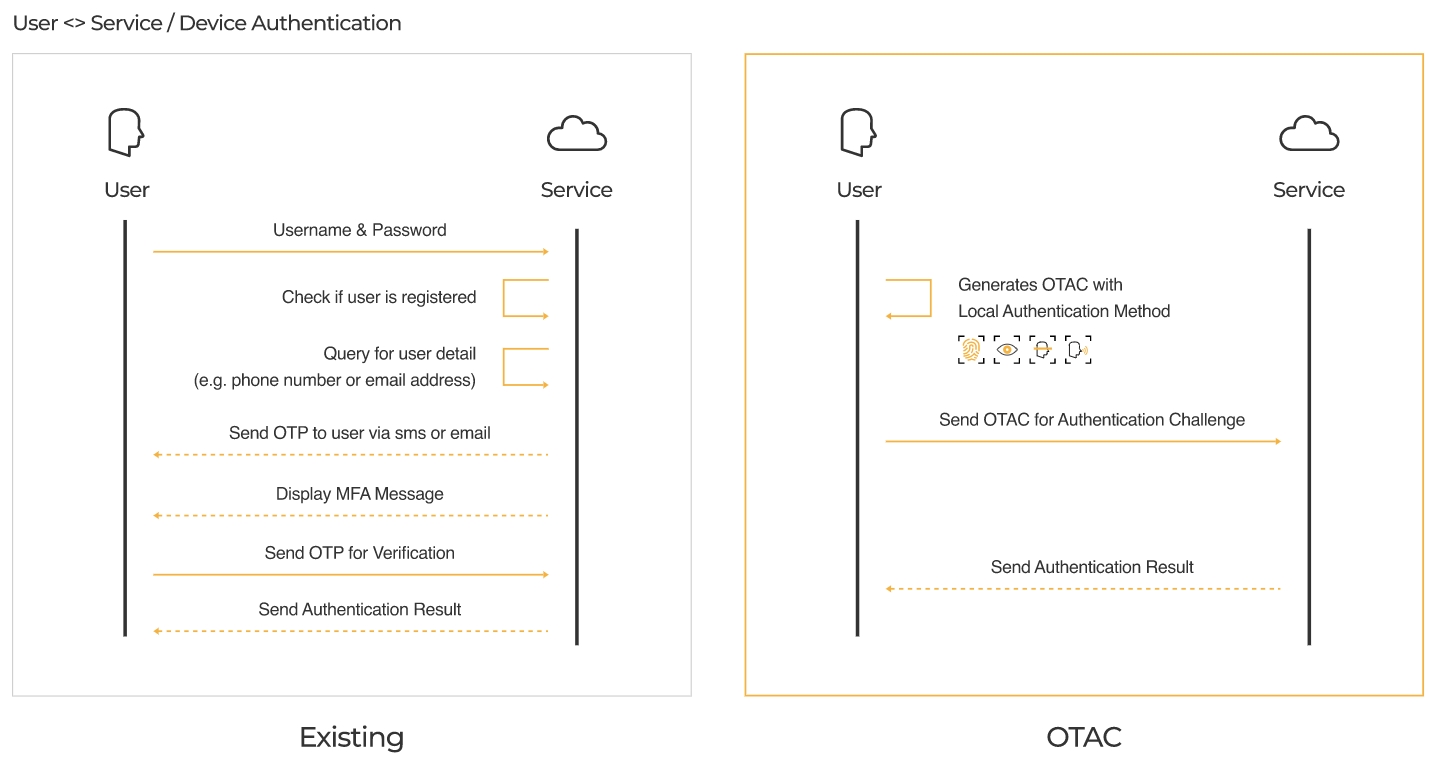
Traditional Two-Way Dynamic Tokens vs One-Way Dynamic Tokens
The One-Time Authentication Code (OTAC) is the world’s first one-way dynamic token technology, designed to overcome the structural limitations of conventional two-way token systems. With OTAC, the client can generate authentication codes independently, using a pre-registered unique key—no real-time communication with the server is required. These codes are transmitted in a single direction to the server, enabling both user identification and verification at once. This approach significantly reduces reliance on network connectivity and lightens the server workload.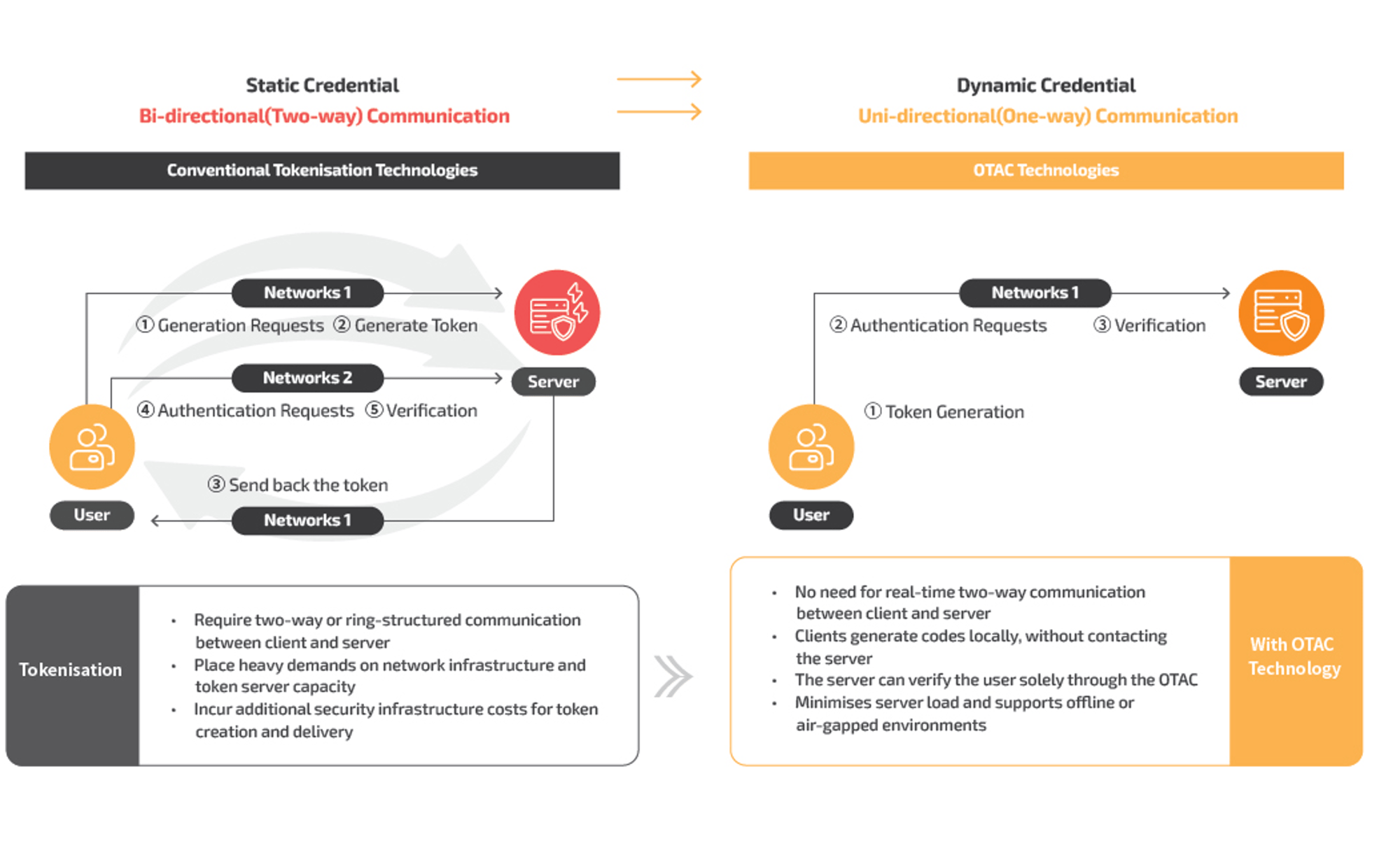
Physical access control
The security hole of radio-frequency identification (RFID) cards is as a result of using static key values. If stolen, all other cards can become exposed. Access control cards using OTAC, on the other hand, generate dynamic codes in regular intervals through a mobile app, allowing safer access control by copying these in a near-field communication (NFC) card. Dynamic codes used in authentication are only available for a certain period, preventing their misuse when duplicated or lost.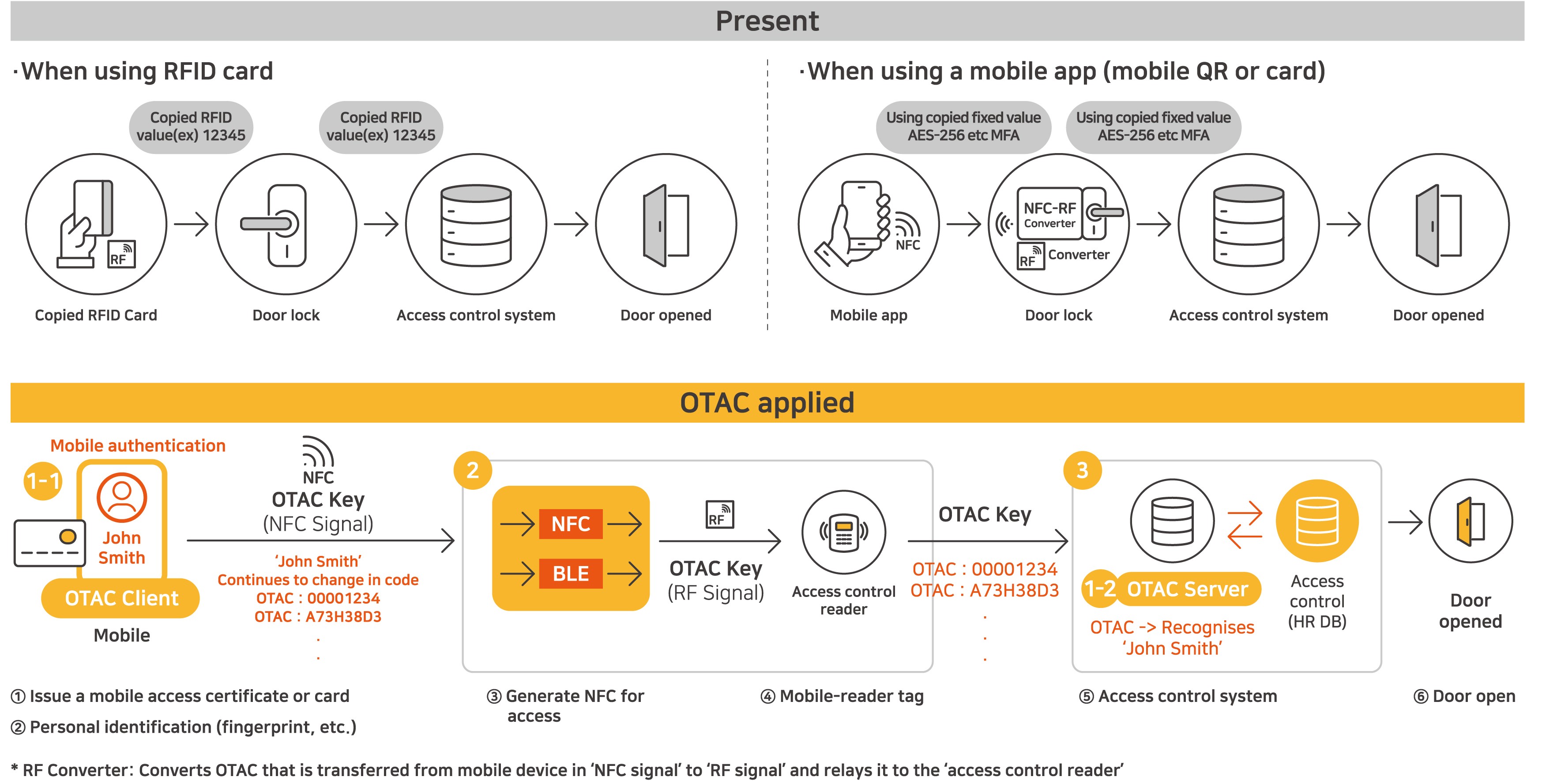


OTAC for enterprise
With OTAC, users can generate dynamic one-time access codes from their own mobile devices. This works in an off-the-network environment. As a result, enterprises can reduce network traffic and enable secure, reliable access management as there is no surface for hackers to attack.
Furthermore, employees and their devices can be identified with the code alone. Therefore, employees no longer have to deal with IDs, passwords and tokens. Also, there is no need to force employees to change their password regularly because OTAC itself is a dynamic code that changes every time!
Why swIDch
that provides all of the following features, tested and substantiated
by the University of Surrey technical report
sufficient to IDENTIFY user
and AUTHENTICATION
off-the-network environment
Single-step identification and authentication with the code alone. Include our biometric option and get single-step MFA. Vastly improved UX by removing steps.
OTAC is a dynamic code, which means the code is constantly changing. Eliminates all use of static information. Forget usernames and passwords forever. Vastly reduced workload for IT helpdesks.
No network connection required for generating OTAC, enabling uninterrupted use no matter where you are. No more waiting for additional tokens/OTPs and no need for heavy public key infrastructure (PKI).
Highly configurable code parameters and lightweight SDK/applet means wide range of deployment options on many devices across multiple sectors.