The OTAC Trusted Access Gateway (TAG) is a plug-and-play solution that brings strong, centralised authentication to operational technology (OT) environments. It protects critical infrastructure—such as PLCs, HMIs, RTUs and DCSs—from unauthorised access by replacing static credentials with one-time authentication codes (OTAC), without requiring replacement of legacy devices or manufacturer-dependent modifications. It also functions as a secure endpoint protection solution by controlling access directly at the device level—ensuring only authenticated users can configure or operate OT endpoints such as PLCs and HMIs.
Stronger Authentication, Minimal DisruptionThe Solution
Powered by swIDch’s patented OTAC technology, the Trusted Access Gateway generates dynamic, non-reusable codes via registered user devices—such as smartphones, smart cards or secured laptops. These codes cannot be reused, shared or stolen, ensuring secure authentication without complex infrastructure changes.
Unlike traditional solutions such as PKI or biometrics, OTAC requires no stored credentials or two-way communication. It even works offline, making it ideal for isolated or air-gapped environments in critical infrastructure.
By securing the link between the user and the endpoint device itself, the Trusted Access Gateway offers granular protection for PLCs, HMIs and other OT assets—without requiring software installation or replacement of the legacy device itself.
How It Works
Understanding how OTAC Trusted Access Gateway functions is key to appreciating its seamless integration and security advantages—here’s a simple breakdown of the process:
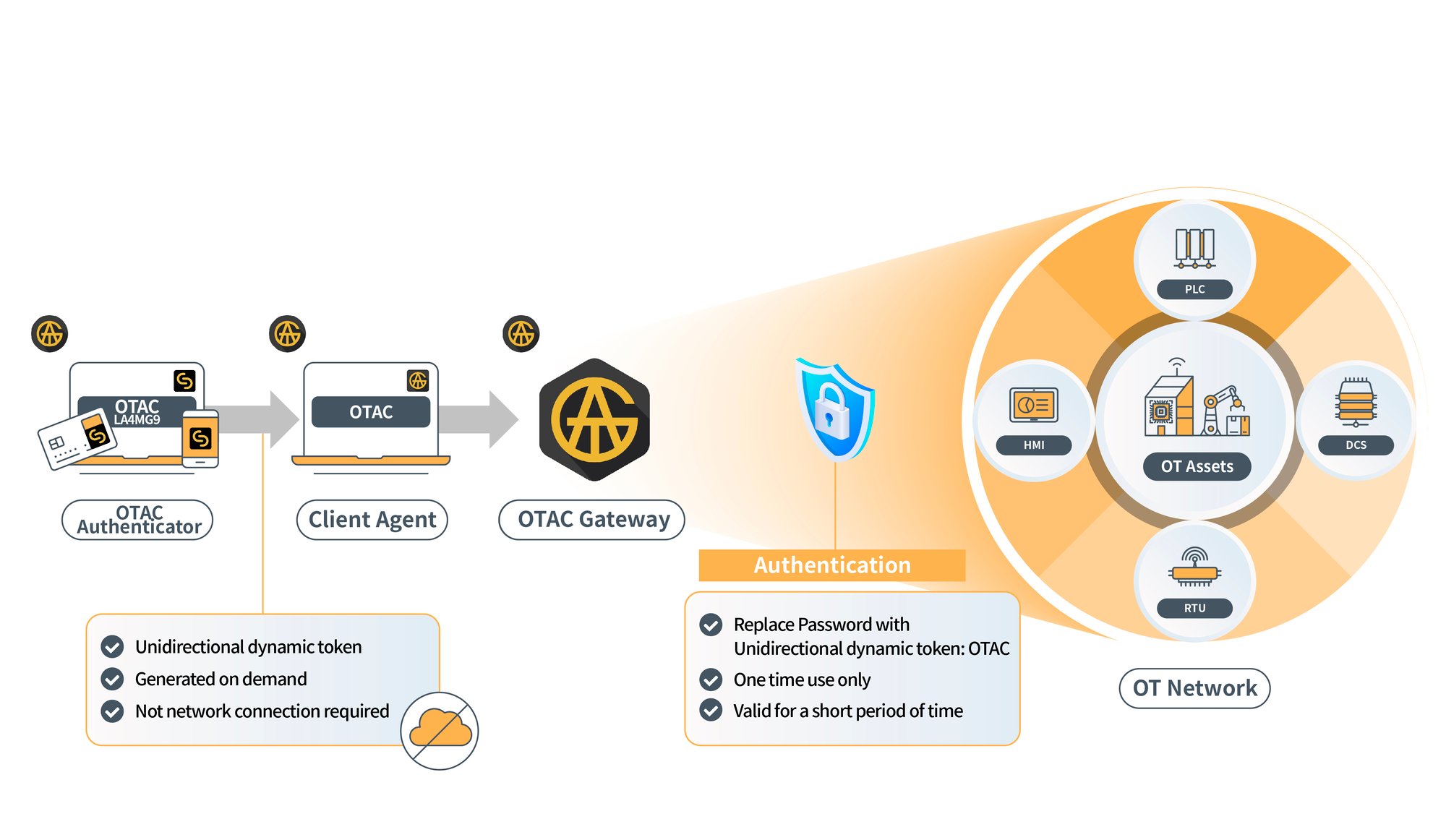
- OTAC Gateway placement: The OTAC Gateway is deployed between the PC/Laptop and the OT system it is trying to access.
- Authentication Request: When a target PLC/HMI/RTU/DCS engineering application is launched, the Client Agent requests the registered user device to complete the multi-factor authentication (MFA) process.
- OTAC Generation: The user generates an OTAC on their registered personal device (e.g., smartphone or smart card) and enters it into the input field.
- Validation: The OTAC Gateway validates the entered code and grants access if the user is authorised. access activity.
This ensures access is validated at the gateway layer before commands or changes reach the endpoint, adding a critical layer of protection for physical control devices.
Key Benefits
The OTAC Trusted Access Gateway provides a seamless upgrade to OT authentication environments without complex system modifications.
- No Need to Replace Legacy PLCs: The PLC devices remain intact, with no vendor firmware changes required.
- Endpoint-Level Security: Secure access is enforced at the device interface, allowing precise control over who can interact with critical OT components such as PLCs, HMIs and RTUs.
- Centralised Management: User authentication can be centrally managed for enhanced control.
- One-Way Dynamic Authentication Codes: Static passwords are replaced with dynamic codes that change for each session, ensuring secure user and device authentication.
- Comprehensive Access Logs: Unlike standard PLC access logs that lack user/device identification, OTAC Trusted Access Gateway’s logs provide meaningful, actionable records of access activity.
Compliance-Ready
The OTAC Trusted Access Gateway helps you meet the world’s leading OT cybersecurity regulations:

- NIS2 – Replaces static passwords with dynamic authentication
- NERC CIP – Enforces role-based and multi-factor access
- IEC 62443 – Aligns with FR1: Identification and Authentication Control
- Cyber Resilience Act (CRA) – Ensures secure and auditable access
And by delivering secure endpoint authentication without altering device firmware or requiring internet connectivity, the solution aligns with zero-trust principles for industrial environments.

Contact us today
OTAC Trusted Access Gateway (TAG) FAQs
-
No. The OTAC Trusted Access Gateway integrates seamlessly without altering your current devices or systems.
-
Unlike PKI, OTAC doesn’t require certificate management or bidirectional communication. Each code is generated locally, making it simpler and more resilient in OT environments.
-
Registered smartphones, smart cards or laptops can generate the dynamic codes required for access.
-
No. Codes are generated independently on the user’s device—no network is needed.
-
Yes. The OTAC Trusted Access Gateway provides detailed access logs that include user and device information, improving auditability.
-
Absolutely. It supports compliance with NIS2, IEC 62443, NERC CIP and the Cyber Resilience Act (CRA).
Why swIDch
that provides all of the following features, tested and substantiated
by the University of Surrey technical report
sufficient to IDENTIFY user
and AUTHENTICATION
off-the-network environment
Single-step identification and authentication with the code alone. Include our biometric option and get single-step MFA. Vastly improved UX by removing steps.
OTAC is a dynamic code, which means the code is constantly changing. Eliminates all use of static information. Forget usernames and passwords forever. Vastly reduced workload for IT helpdesks.
No network connection required for generating OTAC, enabling uninterrupted use no matter where you are. No more waiting for additional tokens/OTPs and no need for heavy public key infrastructure (PKI).
Highly configurable code parameters and lightweight SDK/applet means wide range of deployment options on many devices across multiple sectors.
![[swIDch] OTAC TAG-1](https://www.swidch.com/hubfs/%5BswIDch%5D%20OTAC%20TAG-1.jpg)
![[swIDch] OTAC TAG-2](https://www.swidch.com/hubfs/%5BswIDch%5D%20OTAC%20TAG-2.jpg)



