TAP OTAC - Fraud-Resistant Authentication
swIDch’s TAP OTAC proactively prevents financial fraud, such as phishing, by isolating media from cyberattacks. The OTAC module, generating a financial payment authentication code, is embedded into the payment card's IC chip and financial app as an applet and software development kit (SDK).
Authentication is effortlessly performed by lightly tapping the payment card on the back of a smartphone with a financial app installed. Utilising a dynamic code newly generated each time ensures a robust yet simple authentication process, significantly enhancing user convenience. Additionally, it is compatible with any mobile device's operating system (OS) and facilitates authentication without a separate cellular network.
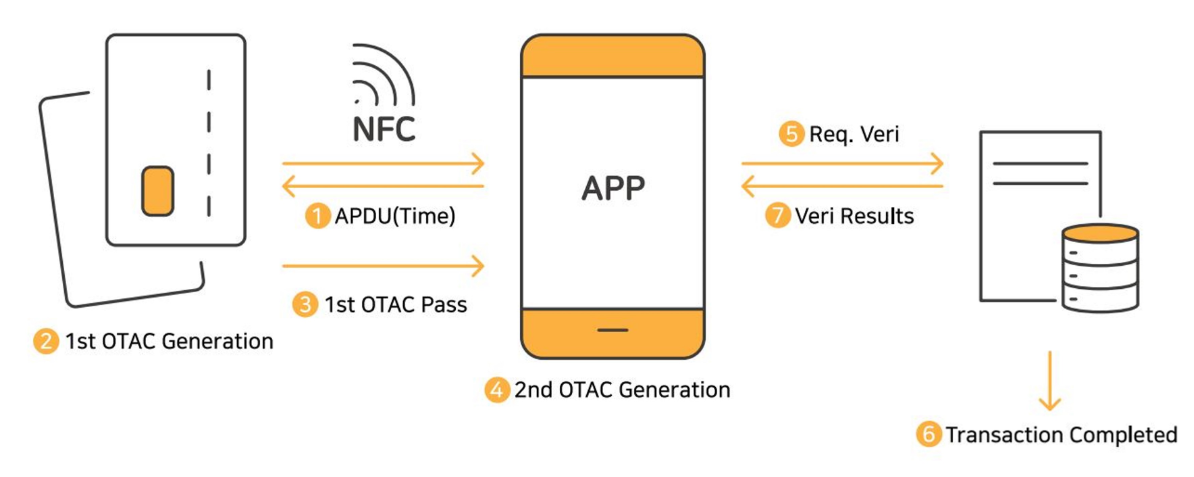
TAP OTAC - How it Works
The card, embedding the OTAC applet, generates the initial OTAC via smartphone near field communication (NFC). As the primary code from the card produces a secondary OTAC through linkage with the app, there is no risk of hacking by stealing the seed value in memory or any potential sniffing risks within the NFC section.
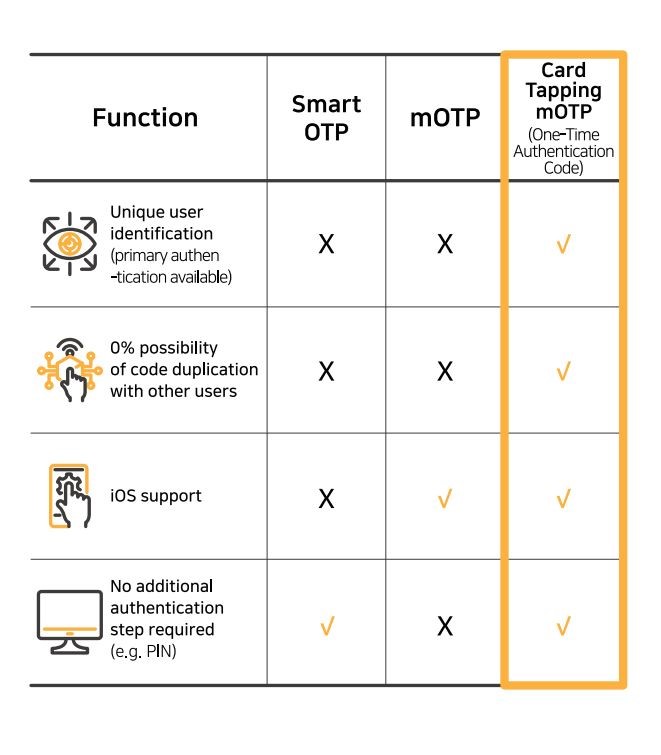
swIDch's TAP OTAC authenticates users by tapping a card embedded with the OTAC applet to a mobile device. This prevents hackers from misusing stolen personal information to generate new OTPs or access financial services. Crucially, flawless user identification and authentication are possible without any chance of code duplication with other users.
TAP OTAC Benefits
Boosting customer loyalty with Secure Transactions
Improved Security with Zero-Trust Fraud Prevention
Multi-Purpose Authentication Beyond Payments
TAP OTAC Banking Case Studies
Contact us today
TAP OTAC Banking FAQs
-
OTAC stands for One-Time Authentication Code. It is used in banking as a secure and innovative authentication method that increases transaction security by generating unique, single-use codes for user verification.
-
OTP stands for One-Time Password. This is a temporary code used to verify a user's identity during online banking transactions. However, OTPs are at higher risk of being stolen by hackers, which can result in financial fraud.
-
The rise of digital financial services has brought convenience but also new security threats. Cybercriminals continuously evolve their tactics, using phishing (smishing and voice phishing), card misuse, and personal information theft. Even with multi-factor authentication (MFA) solutions like mobile OTP and biometric authentication, sophisticated fraud techniques remain a challenge to prevent.
-
Phishing scams often lead to hijacked accounts, unauthorized transactions, and financial fraud. Criminals install remote control apps to steal login credentials, leaving mobile financial environments vulnerable. In the U.S., 75% of all fraud losses come from consumer phishing, with institutions spending $4.23 in response costs for every $1 lost.
-
Many users experience delays, non-receipt of authentication codes, or cumbersome extra steps like one-time passwords (OTP), ARS verification, or device registration. When these services fail, users must contact customer service, leading to frustration—especially in off-network environments where SMS and ARS authentication are inaccessible.
-
Financial fraud recovery varies across industries like banking, telecommunications, and e-commerce. Each case requires legal and financial investigations to determine liability and compensation, making the process complex and time-consuming. Despite regulatory efforts, preventing fraud entirely remains difficult due to its ever-evolving nature.
Why swIDch
that provides all of the following features, tested and substantiated
by the University of Surrey technical report
sufficient to IDENTIFY user
and AUTHENTICATION
off-the-network environment
Single-step identification and authentication with the code alone. Include our biometric option and get single-step MFA. Vastly improved UX by removing steps.
OTAC is a dynamic code, which means the code is constantly changing. Eliminates all use of static information. Forget usernames and passwords forever. Vastly reduced workload for IT helpdesks.
No network connection required for generating OTAC, enabling uninterrupted use no matter where you are. No more waiting for additional tokens/OTPs and no need for heavy public key infrastructure (PKI).
Highly configurable code parameters and lightweight SDK/applet means wide range of deployment options on many devices across multiple sectors.


