A comprehensive guide to secure operational technology (OT)

In today's interconnected world, Operational Technology (OT) faces increasing security challenges as network connectivity expands. Unlike Information Technology (IT), which primarily deals with business processes and data, OT involves devices that physically interact with the real world. This distinction necessitates tailored security approaches for OT environments.
OT networks are no longer isolated via the 'air-gap'
Operational Technology (OT) encompasses systems where physical devices directly interact with the real world. While OT networks have traditionally been isolated through air-gaps, the growing need for connectivity has eroded this isolation, exposing them to security threats. OT systems are highly automated and operated by multiple devices, with limited interconnectivity among internal users, external operators, devices, and workloads. To enable Identity and Access Management (IAM) services within OT environments, IT-operated IAM services must be adapted to account for the unique characteristics of OT systems.
OT & IT security objectives differ greatly
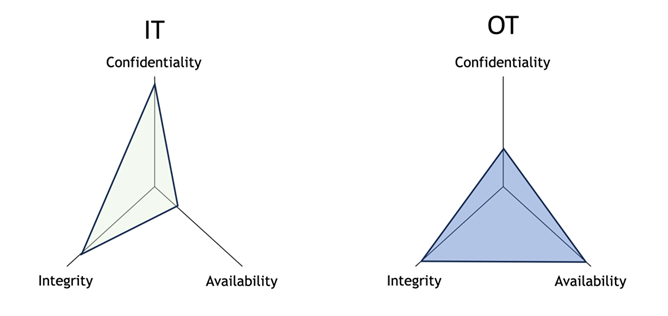
OT security and IT security diverge in terms of their objectives and focus areas. OT cybersecurity primarily aims to ensure the availability and safety of critical equipment and processes. Its primary concern is maintaining the uninterrupted operation of physical systems, as disruptions can result in substantial financial losses. On the other hand, IT cybersecurity primarily emphasizes confidentiality, safeguarding sensitive data during storage and transmission.
Why you should never use password based auth in OT environments
Managing individual access based on password authentication in OT environments presents limitations and challenges. To address these issues, organizations can turn to dynamic authentication technologies instead of solutions reliant on static information, which offer improved security for password-based authentication. Because ICSs are often limited in adapting higher security stacks due to their low computing output, the password-based credential is commonplace and still being used as an authentication mechanism for human users and processes. However, passwords bring with them significant challenges.
Typical challenges are:
- Password sharing (where users not uniquely defined - not recommended)
- Password management between ID/PW specified for each OT device
- Difficulty managing user changes (leavers/contractors)
- Inherent password weaknesses (static information vulnerable to brute forcing, phishing, credential stuffing etc)
Benefits of device-to-device authentication using PSK
When determining the appropriateness of user and device authentication technologies for the Industrial IoT, the choice between PSK (Pre-Shared Key) and PKI (Public Key Infrastructure) depends on several factors. Consider the following guidelines:
Scale and Complexity: If the Industrial IoT deployment involves a relatively small number of devices and requires simplicity in key management, PSK may be more appropriate. However, if the deployment is large-scale and requires a flexible, scalable authentication infrastructure, PKI is generally a better choice.
Security Requirements: Assess the security needs of the Industrial IoT application. If robust authentication, strong identity verification, and granular access control are critical, PKI is often the preferred option. PKI's ability to provide digital certificates and a hierarchical trust model offers more advanced security features compared to PSK. OT systems are running in various environments with different confidentiality levels. The choice should be based on a thorough analysis of the use case and a consideration of the trade-offs.
Resource Constraints: Consider the computing resources and limitations of the IoT devices. PSK is typically more lightweight and computationally efficient, making it suitable for devices with limited processing power or memory. PKI, on the other hand, involves more complex cryptographic operations and may require more substantial resources.
Connectivity and Offline Authentication: Evaluate the connectivity requirements of the Industrial IoT deployment. PSK allows for offline authentication, making it suitable for scenarios where devices may intermittently lose network connectivity. PKI relies on continuous network connectivity to validate certificates, which can be a limitation in certain environments.
Lifecycle Management: Assess the need for device onboarding, revocation, and overall lifecycle management. PKI offers a comprehensive infrastructure for issuing, managing, and revoking certificates, making it easier to handle device provisioning and decommissioning. PSK, while simpler, may present challenges in large-scale deployments that require frequent key rotation or revocation.
Ultimately, the selection of the appropriate authentication technology for Industrial IoT should be based on a careful evaluation of the specific requirements, security considerations, scalability needs, and resource constraints of the deployment.
Device-to-device authentication is a critical aspect of securing OT environments. In simplified operating environments running with limited computing resources, the PSK method of authentication offers stronger availability, focusing on ensuring secure and highly reliable communication between devices rather than confidentiality. Implementing PSK authentication protocols can minimize the risks of unauthorized access or malicious interference, providing a robust authentication mechanism for OT systems.

Key aspects of device-to-individual authentication
Device-to-individual authentication in OT environments requires careful consideration, particularly in situations where high-level Human-Computer Interface (HCI) access needs to be granted to 3rd party external operators at specific times. To address this challenge, organizations should consider granting just-as-enough and temporary access to external operators in need. Implementing a PSK-based authentication token that remains valid for a limited period offers a practical solution, ensuring secure and controlled access for authorized personnel during operational tasks.
Tailored authentication solutions are the answer
As OT environments become increasingly interconnected, organizations must adopt robust security measures to safeguard critical equipment and processes. By recognizing the distinct characteristics and objectives of OT security, tailored authentication solutions can be implemented. The Pre-Shared Key (PSK) method provides a reliable approach for device-to-device authentication, while granting temporary access through PSK-based authentication tokens ensures controlled access for individuals in OT environments. With these solutions in place, organizations can enhance the security posture of their OT systems and mitigate the evolving threats they face.
--------------------

Author: Sangchual Cha (Head of Engineering)
With over 20 years experience as a software engineer working for some of the worlds biggest companies including Amazon, Sang uses his knowledge and expertise to progress swIDch's technology and provide detailed insight to global audiences at swIDch and beyond.
--------------------

swIDch will continue its quest to innovate and pioneer next-generation authentication solutions. To stay up-to-date with the latest trends sign up to our newsletter and check out our latest solutions.

At a large industrial site, a contractor needed temporary access to a controller to complete routine maintenance. The

At a large manufacturing plant in Northern Europe, a routine maintenance task nearly became a shutdown. An external

For many OT organisations, Passwordless still feels abstract. The concept is attractive — fewer credentials, fewer
Looking to stay up-to-date with our latest news?