(Part 4) Key security vulnerabilities in IoT environment and how to effectively counteract them
Welcome to the final instalment, part 4 of our IoT security vulnerabilities blog series. As I’ve mentioned in previous series articles, there are many challenges facing the modern day IoT environment, for example:
- Difficulty to update firmware in many IoT devices
- Plaintext based IoT protocol
- Illegal access to IoT devices to exfiltrate and tamper data
- Dangerous authentication mechanism using ID and Password
- Unstable and closed network environment
Many companies are considering applying PKI or FIDO technology to address the issues.
To this extent, I’m going compare our One-time-authentication-code (OTAC) technology and highlight our advantages over other technologies.
Without PKI, the secure data transport between clients and applications would be extremely complex, since every application should devise its own mechanisms for transporting data securely between them.
As useful as PKI is, FIDO protocols have a few advantages over PKI.
FIDO is simpler for end-users to use, and for application developers to integrate into web and mobile applications.
Even more useful than PKI and FIDO, OTAC is a 'simple to implement' authentication system for IoT environments.
Let’s take a look at the registration and authentication process between OTAC and FIDO.
Registration process
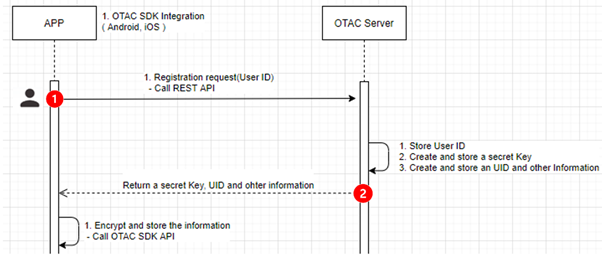
Figure. Registration process for OTAC
Step 1) Initiate registration by sending user’s unique information such as User ID and System ID etc and create a secret key and other related information by using User ID and other information.
Step 2) Send them back to user’s device.
FIDO on the other hand, works as follows.
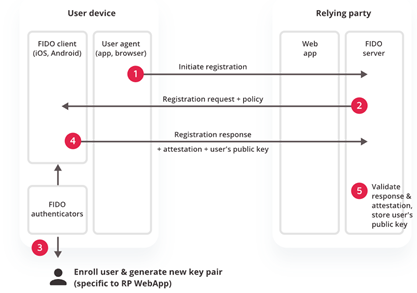
Figure. Registration process for FIDO
Step 1+2) Initiate registration
Step 3) User’s device creates a new public/private key pair unique for the local device, online service and user’s account after initiating registration process.
Step 4) Public key is sent to the online service and associated with the user’s account. The private key and any information about the local authentication method (such as biometric measurements or templates) never leave the local device.
(https://fidoalliance.org/how-fido-works/)
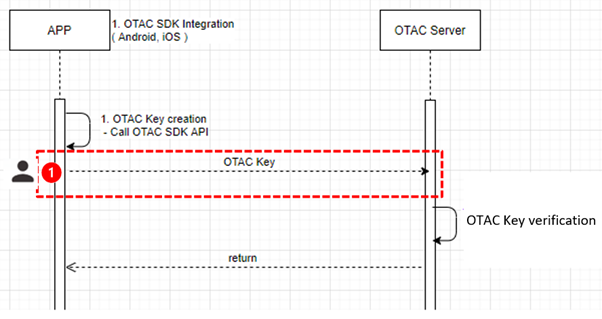
Figure. Authentication process for OTAC
1) User’s device sends OTAC once after creating OTAC authentication key and then OTAC server would verify the key.
Whereas FIDO works as follows.
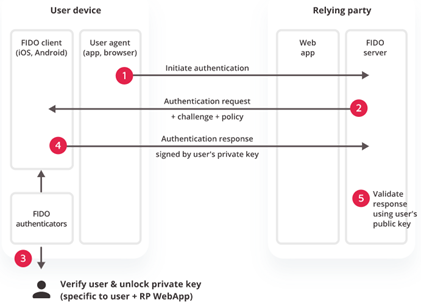
Figure. Authentication process for FIDO
Step 1), 2) Online service challenges the user to login with a previously registered device that matches the service’s acceptance policy.
Step 3) User unlocks the FIDO authenticator using the same method as at Registration time.
Step 4) Client device sends the signed challenge back to the service, which verifies it with the stored public key and logs in the user.
What’s the difference between the two?
OTAC communication is unidirectional, so OTAC only issues a verification request to the server.
However, FIDO communication is bidirectional, so FIDO requires challenge and response.
What’s the advantage in using OTAC?
Companies are often faced with a range of issues when they try to implement FIDO or PKI in IoT.
As I've already highlighted, IoT traffic needs to be quick and lightweight.
FIDO and PKI add an additional round trip to the start of every session.
Depending on the distance between the monitoring server and IoT devices or the latency of IoT devices, this can mean the communication latency increases. If using a closed network and/or slow network, companies would no longer be able to use FIDO and PKI effectively.
To highlight the competitive advantage of OTAC further, swIDch recently announced that its OTAC technology will support PERURI’s Digital Transformation in Indonesia. The aim is to provide our unique OTAC technology as an authentication in line with the organization’s overall digital transformation business.
Why did the Indonesian government chose OTAC technology?
Geographical aspect: Indonesia has so many islands, which results in a very low internet penetration rate compared to other countries.
Our patented algorithm, OTAC (one-time authentication code) can provide authentication mechanisms in a network-less or unstable environment. It provides an instantaneous, lightweight and strong authentication mechanism in IoT environments as well as common IT environments, making it the perfect fit for our partners in Indonesia.
--------------------
About Charlie Choi
Charlie Choi is a technical director and a security advisor at SSenStone. He's been working in security consulting, application security and cloud security for over 20 years during which he has authored several books and a multiple expert papers. He has a Master of Industrial and information engineering from Soongsil University, Korea.
Looking to stay up-to-date with our latest news?