Admin
Popular
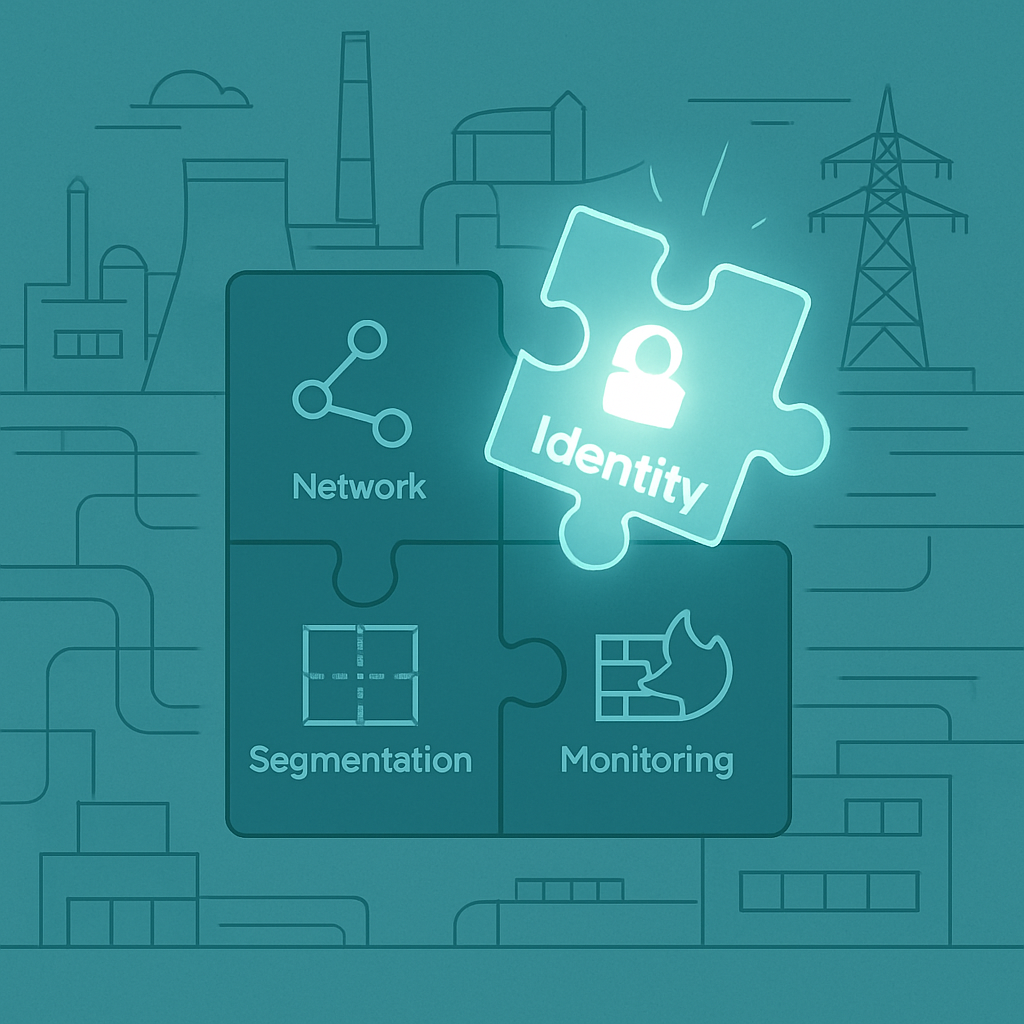
Even after a year filled with operational technology (OT) security investments, audits, and...

Across industries, Operational Technology (OT) leaders are preparing 2026 budgets with one priority...

When a major U.S. steelmaker halted part of its production after a cyber incident in May 2025,...

In late October 2025, the Canadian Centre for Cyber Security issued an unusual public alert....

A recent cyberattack on Jaguar Land Rover forced the temporary closure of its Solihull, Halewood...

In October 2025, the European Union Agency for Cybersecurity (ENISA) reported that 18.2 % of all...

With 2026 approaching, many organisations are facing a difficult question: how can they strengthen...

As organisations approach the end of 2025, leaders are finalising strategies and budgets for the...

Cyber security in operational technology (OT) has entered a new era. Ransomware groups are now...

Industrial operations are rapidly moving towards digitalisation, and control systems are no...
Looking to stay up-to-date with our latest news?
