Many industrial sites still rely on legacy, password-based equipment and air-gapped networks. As external connectivity increases, fixed-value authentication poses serious risks. OTAC Auth MFA, powered by SSenStone’s patented OTAC (One-Time Authentication Code) technology, delivers strong multi-factor authentication across critical OT endpoints including SCADA, HMIs, industrial PCs, PLCs and actuators.
Easy deployment with minimal modifications
OTAC Auth MFA consists of the OTAC Verifier SDK and OTAC Authenticator, enabling end-users to develop and implement MFA directly.
- Embed the Verifier SDK into SCADA, HMI, industrial PCs or other configurable equipment
- Install the Server Module within the OT network
- Users generate an OTAC on a registered device (app, OTAC display card, biometric USB, etc.) and enter it
- The endpoint forwards the OTAC to the Server Module
- The server verifies and authorises access
This approach makes it simple to customise to enterprise needs. Session triggers (screen entry, high-risk commands, pre-deployment), role- or task-based policies, UX flows and audit logging can all be tailored. With a local-first verification structure, continuity is ensured even in air-gapped or offline environments — making OTAC Auth MFA ideal for organisations with in-house or partner development capacity that require flexible alignment with processes, interfaces and access rights.
OTAC Auth MFA Authentication Procedure
Users authenticate by entering an OTAC generated on their registered device — such as a smartphone, smart card or biometric USB. This enables secure MFA without complex infrastructure changes.
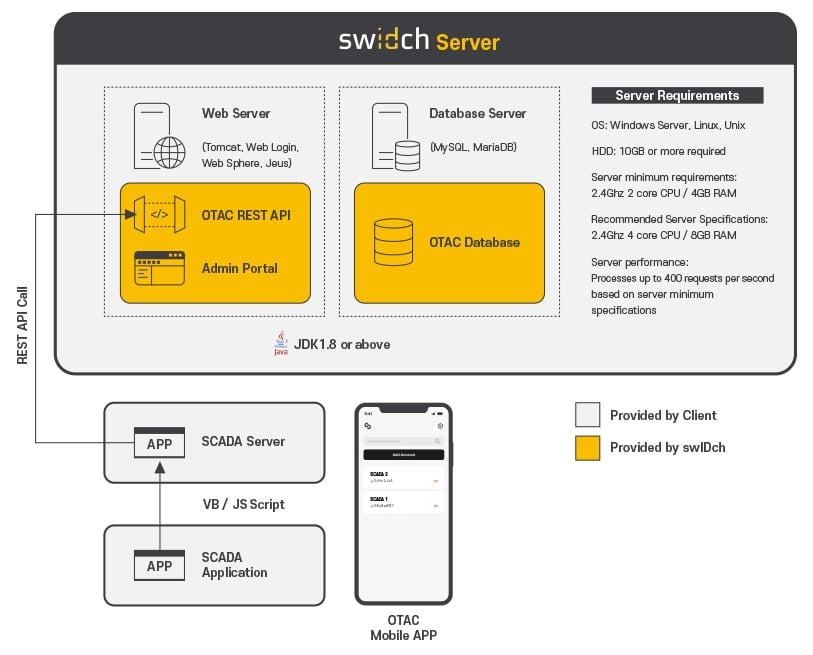
- Deployment: The OTAC Verifier (verification server) is installed within the client’s infrastructure. OT equipment requiring authentication (e.g. SCADA, HMI, actuators) is configured via the engineering programme to forward OTACs to the verification server.
- Authentication Request: The OTAC entered through the engineering programme is transmitted to the verification server to complete MFA.
- OTAC Generation: The user generates a one-time, one-way dynamic authentication code (OTAC) on their registered device, then enters it into the authentication field.
- Verification: The verification server checks the OTAC. If authorised, the critical device receives approval and grants access.

👉 Each session is dynamically verified, preventing reuse, sharing or theft of credentials.
OTAC Auth MFA Deployment Architecture
OTAC Auth MFA can be implemented easily in a wide range of OT system environments. For example, installing the OTAC verification module on a SCADA server allows the existing password input field to be replaced with an OTAC input field — enabling MFA immediately.
Why OTAC Auth MFA?
Many organisations remain constrained by legacy equipment and air-gapped environments. OTAC Auth MFA provides practical and sustainable protection that fits these realities:
- Multi-factor authentication for OT endpoints: Safeguards SCADA, HMIs, PLCs and other critical devices
- Legacy compatibility: Implements MFA without replacing existing equipment
- Air-gapped and offline support: OTAC generation and verification work without internet connectivity
- Flexible policy design: Tailor roles, task-based policies, UX and audit logging


Contact us today
OTAC Trusted Access Gateway (TAG) FAQs
-
Yes. OTAC Auth MFA supports non-invasive deployment — it adds multi-factor authentication to existing PLCs, HMIs, and other industrial devices without hardware or firmware replacement, ensuring zero downtime.
-
Absolutely. OTAC Auth MFA is designed with a local-first verification structure, allowing full authentication even in air-gapped or disconnected environments, which makes it ideal for critical infrastructure sites.
-
-
PLC OTAC: MFA is pre-installed by OEMs during production — best for device manufacturers embedding security.
-
OTAC Trusted Access Gateway (TAG): MFA is added inline at the network level — best for operators wanting full coverage without modifying existing assets.
-
OTAC Verifier SDK & Authenticator: MFA is developed directly by end-users — best for organisations seeking custom authentication workflows.
-
-
OTAC Auth MFA supports IEC 62443 FR1 and NIS2 authentication requirements by providing endpoint-level MFA, auditable access logs, and verifiable user–device binding, strengthening compliance readiness.
-
Yes. OEMs can integrate the OTAC Verifier SDK directly into PLC or device firmware. This enables MFA at the factory stage and supports advanced features like device activation, feature flag control, SKU differentiation, and remote provisioning.
-
The OTAC Trusted Access Gateway (TAG) supports inline or bypass modes, allowing MFA deployment across multiple network paths without downtime, ensuring continuity for production and maintenance operations.
-
OTAC MFA combines:
-
Something you know: PIN/password
-
Something you are: Biometric authentication
-
Something you have: The OTAC — a one-time, dynamic code generated by a trusted device
This combination provides strong, non-replayable multi-factor authentication.
-
-
Typical adopters include:
-
Industrial operators modernising legacy SCADA and PLC systems
-
Manufacturers (OEMs) embedding built-in MFA
-
Integrators and engineering teams requiring tailor-made, policy-based access control for complex OT networks
-
Why swIDch
that provides all of the following features, tested and substantiated
by the University of Surrey technical report
sufficient to IDENTIFY user
and AUTHENTICATION
off-the-network environment
Single-step identification and authentication with the code alone. Include our biometric option and get single-step MFA. Vastly improved UX by removing steps.
OTAC is a dynamic code, which means the code is constantly changing. Eliminates all use of static information. Forget usernames and passwords forever. Vastly reduced workload for IT helpdesks.
No network connection required for generating OTAC, enabling uninterrupted use no matter where you are. No more waiting for additional tokens/OTPs and no need for heavy public key infrastructure (PKI).
Highly configurable code parameters and lightweight SDK/applet means wide range of deployment options on many devices across multiple sectors.



