When a Cyberattack Tests the Limits of Automotive OT Security

A recent cyberattack on Jaguar Land Rover forced the temporary closure of its Solihull, Halewood and Wolverhampton plants — a disruption estimated to cost the UK economy £1.9 billion. For weeks, vehicles could not roll off the lines, components piled up, and suppliers struggled to stay afloat.
It was not the first industrial cyberattack, but perhaps the most visible sign that modern car manufacturing has become critically dependent on digital trust.
The Digital Anatomy of a Modern Car Plant
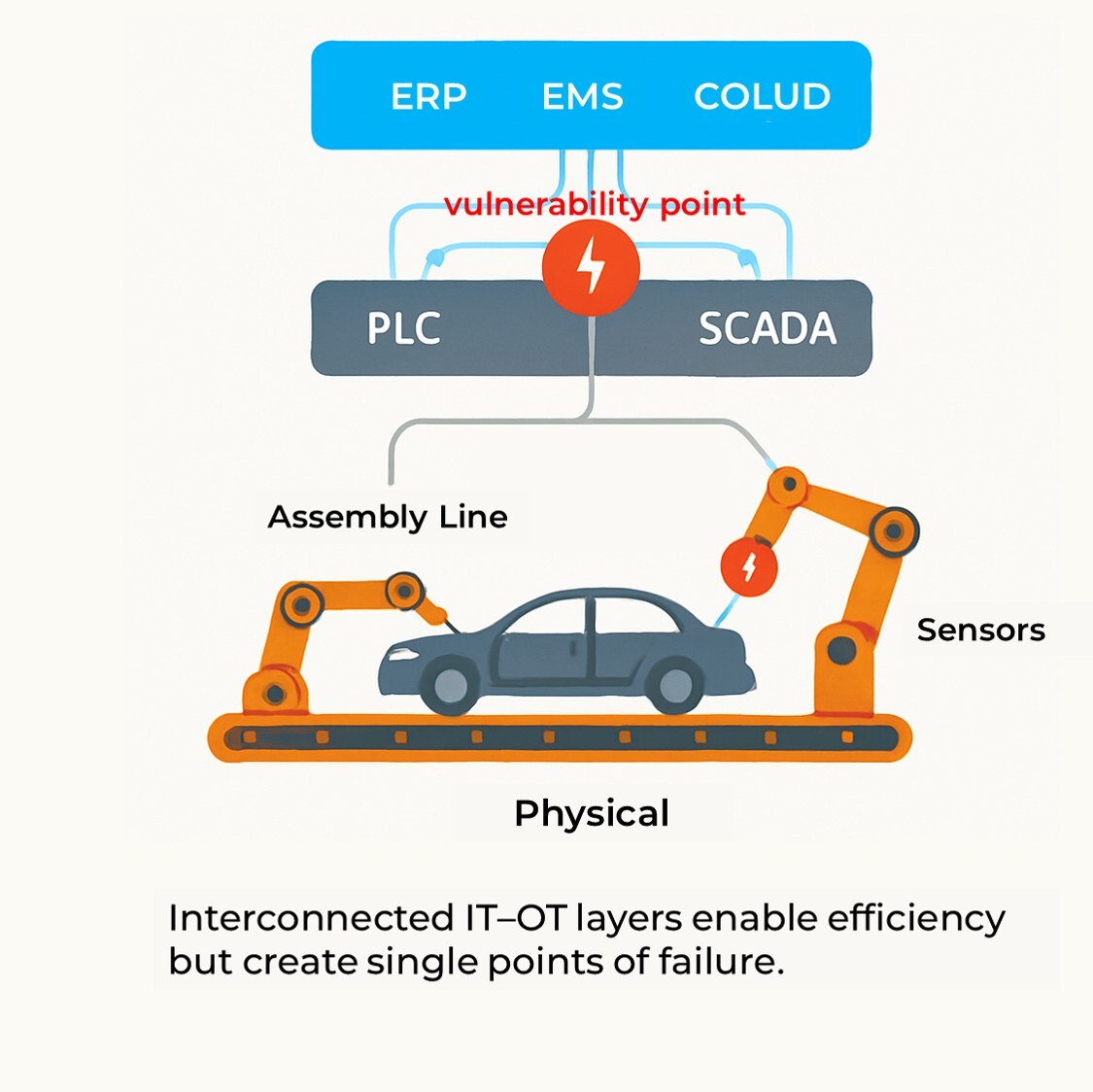
A car factory today is no longer a set of mechanical lines controlled by human operators. It is an intricate digital organism.
- Programmable Logic Controllers (PLCs) drive robotic welding cells that perform thousands of precision joints per hour.
- Manufacturing Execution Systems (MES) synchronise body shops, paint booths and assembly halls in real time.
- Supply-chain systems link tier-one and tier-two suppliers to inbound logistics, ensuring that brake modules, ECUs, and seat frames arrive exactly when needed — not a moment earlier or later.
- Connected testing and inspection rigs feed telemetry back into cloud analytics for quality assurance and predictive maintenance.
This interconnectedness between operational technology (OT) and information technology (IT) has transformed efficiency and productivity — but also created a single, fragile surface of attack.
Why the Attack on One OEM Shook an Entire Ecosystem
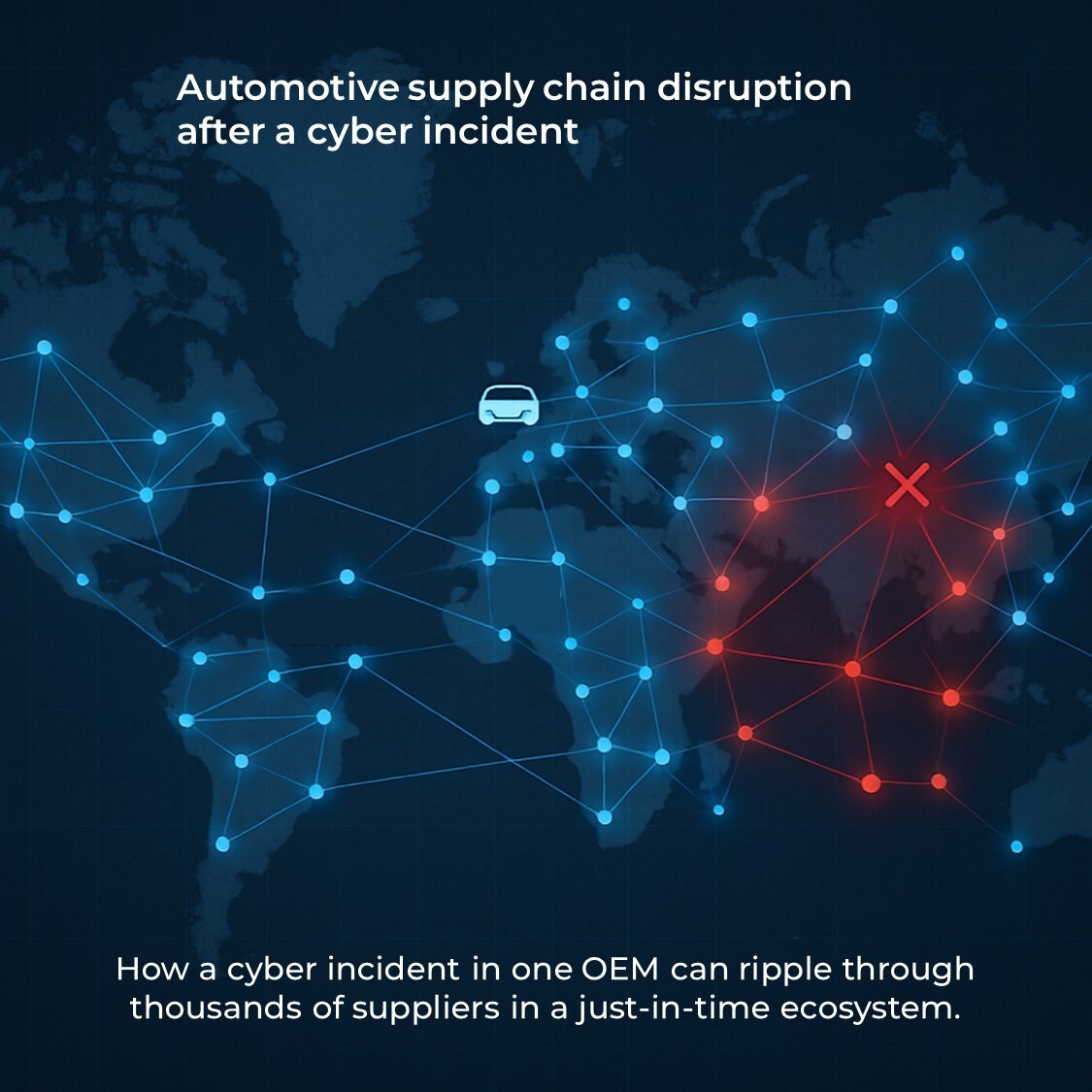
Reports from the UK’s Cyber Monitoring Centre indicate that more than 5,000 businesses were affected by the JLR shutdown, from stamping plants to local transport firms.
That scale of impact is only possible in a sector built around just-in-time production and digitally synchronised supply chains. When a central hub stops, every dependent node idles. A missing batch of steering racks or a halted paint booth can halt production of thousands of vehicles across multiple continents.
In automotive manufacturing, uptime is not a convenience — it is survival. Each hour of downtime can cost tens of millions in lost output, penalties, and reputational damage.
The JLR case illustrates how a breach in the IT domain — a compromised enterprise application, a shared network credential, a vulnerable update server — can ripple into the OT environment where physical motion depends on digital signals.
A Structural Challenge, Not a Single Failure
No manufacturer is immune. Automotive production has evolved under competitive pressure to connect, automate, and remotely manage every layer — from supplier ordering to final inspection.
This evolution outpaced the security design of older systems. Many industrial controllers were never meant to authenticate modern users, log events centrally, or operate safely when isolated from the corporate network.
When defences fail, operators often have no choice but to shut down entire networks to prevent further spread — precisely what happened in this case.
The truth is that the problem is systemic, not localised. It is not that JLR was careless; rather, it was exposed first in an industry where digital convergence has outpaced resilience.
Towards a Resilient Automotive OT Model

Building resilience in automotive operations now demands the same rigour long applied to functional safety:
- Segmentation of production zones — separate control, monitoring and enterprise layers so that a compromise in one does not cascade to another.
- Offline-capable authentication — ensuring engineers and maintenance staff can still verify identity even when central servers are unavailable.
- Comprehensive access logs — enabling audit trails across PLCs, MES and vendor systems, supporting frameworks such as IEC 62443 and NIS2.
- Supplier cybersecurity due diligence — requiring tier partners to meet minimum security baselines for connected tooling and software updates.
- Restoration drills — practising rapid, partial restarts without risking safety or quality.
Some manufacturers have begun adopting dynamic, code-based authentication frameworks that can operate without constant network connectivity or vendor-specific integration — for instance, the OTAC Trusted Access Gateway (TAG) approach — to ensure critical access remains verifiable even during isolation events.
What matters is not the brand, but the principle: authentication that withstands disruption and preserves traceability across every layer of production.
The Broader Lesson
The automotive industry pioneered automation, but in doing so it also became the first to experience how deeply physical production depends on digital integrity.
The events of 2025 should not be read as one company’s failure but as a turning point — proof that resilience must now extend beyond servers and data centres to include the robots, conveyors and controllers that build the world’s vehicles.
Manufacturers that act early — mapping their OT dependencies, enforcing authentication at every layer, and ensuring visibility across all connected assets — will not only prevent downtime but also preserve the trust that underpins modern mobility.
--------------------

swIDch will continue its quest to innovate and pioneer next-generation authentication solutions. To stay up-to-date with the latest trends sign up to our newsletter and check out our latest solutions.

At a large industrial site, a contractor needed temporary access to a controller to complete routine maintenance. The

At a large manufacturing plant in Northern Europe, a routine maintenance task nearly became a shutdown. An external

For many OT organisations, Passwordless still feels abstract. The concept is attractive — fewer credentials, fewer
Looking to stay up-to-date with our latest news?