The Hidden Cost of Delaying OT Security

In October 2025, the European Union Agency for Cybersecurity (ENISA) reported that 18.2 % of all recorded cyber incidents in Europe targeted operational technology (OT) systems, marking a sharp rise from 14 % in the previous year. This steady escalation demonstrates a critical reality: postponing OT security investment no longer saves money — it multiplies loss.
The financial and operational impact of delay stretches far beyond the initial cost of deployment. It includes production downtime, regulatory penalties, rising insurance premiums, and reputational damage that directly affects future contracts and investor confidence.
Operational Disruption and Production Loss

When industrial control endpoints — PLCs, HMIs, or RTUs — are compromised, production downtime becomes immediate and costly.
A single shutdown at a mid-sized manufacturing facility can cost €200,000 to €500,000 per hour, depending on the sector and output scale. In heavy industry or energy operations, those figures can exceed €1 million per hour once safety and recovery processes are triggered.
Beyond the financial cost, there is the human factor: delayed maintenance, disrupted logistics, and strained supplier commitments. For many operators, a one-day outage erases the savings of years of deferred investment.
Regulatory Penalties and Compliance Exposure

Under the NIS2 Directive, critical infrastructure operators are now legally required to demonstrate “appropriate and proportionate technical and organisational measures” — including strong identity and access control for OT environments.
Failure to comply can result in fines of up to 2 % of annual global turnover. For a company with yearly revenue of €1 billion, that could mean a €20 million fine, excluding the cost of legal counsel, remediation, and reputation recovery.
Meanwhile, many organisations facing last-minute audits must outsource rapid compliance work — often paying two to three times the cost of a properly planned deployment.
Insurance Premiums and Financial Risk

Cyber insurers have started differentiating between IT and OT maturity when assessing risk.
Policies covering industrial assets now often require:
- Documented OT asset inventory
- Verified authentication systems
- Demonstrable segmentation between IT and OT networks
Companies lacking these foundations face higher premiums or reduced coverage. According to European insurance market data, firms with minimal OT-security evidence pay on average 30–40 % more in premiums than those with verified controls.
Delaying investment therefore compounds cost — not only through exposure, but through financial instruments meant to mitigate it.
Compounded Reputational and Market Costs
Beyond direct penalties, security delays erode trust.
Suppliers and customers increasingly request proof of compliance with IEC 62443 and NIS2 as part of procurement processes. A single incident, or even a regulatory warning, can disqualify a company from major industrial tenders for several years.
In a 2025 survey of European manufacturers, 62 % said they would reconsider a supplier partnership following a known OT breach.
That reputational loss translates directly into missed revenue — a cost almost impossible to recover once trust has eroded.
Why Acting Now Costs Less
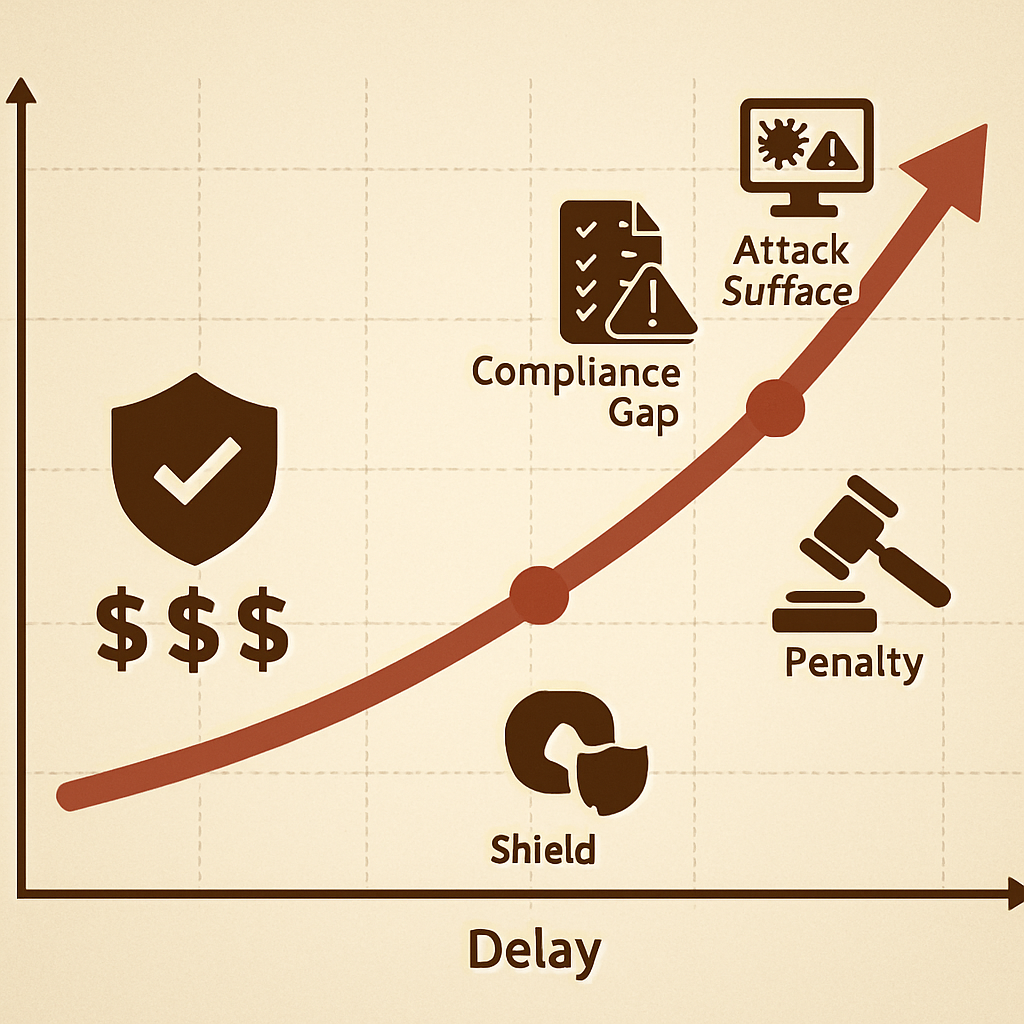
The argument that “we’ll budget for OT security next year” assumes the risk remains constant. It doesn’t.
Every quarter of delay increases the attack surface, the compliance gap, and the potential penalty window. A modest deployment — such as implementing OTAC-based dynamic authentication or segmenting user access — often costs less than one day of unplanned downtime.
Investing now transforms cybersecurity from a defensive expense into a measurable shield for revenue continuity, compliance assurance, and brand integrity.
Delaying OT security doesn’t defer cost — it multiplies it.
--------------------

swIDch will continue its quest to innovate and pioneer next-generation authentication solutions. To stay up-to-date with the latest trends sign up to our newsletter and check out our latest solutions.

At a large industrial site, a contractor needed temporary access to a controller to complete routine maintenance. The

At a large manufacturing plant in Northern Europe, a routine maintenance task nearly became a shutdown. An external

For many OT organisations, Passwordless still feels abstract. The concept is attractive — fewer credentials, fewer
Looking to stay up-to-date with our latest news?