5 uncomfortable truths revealed in the 2025 global OT security reports

The OT and critical infrastructure incidents we witnessed throughout 2025 showed, with unusual clarity, where attackers are aiming and how they are gaining entry. Yet the year’s global OT security reports exposed a deeper, more structural reality: even as regulations mature and technologies advance, the foundations of OT security remain unchanged — and so do the risks.
Across industries and regions, the reports point to the same conclusion: the weaknesses holding OT security back are not hidden in advanced exploits or unknown vulnerabilities, but in the way organisations manage users, devices, accounts, supply chains, and operational structures.
The reports make one point repeatedly: attacks are not becoming more sophisticated — they are becoming more predictable. The same familiar entry paths continue to be abused, and those paths lie not in the heart of OT systems, but around the operational perimeter.
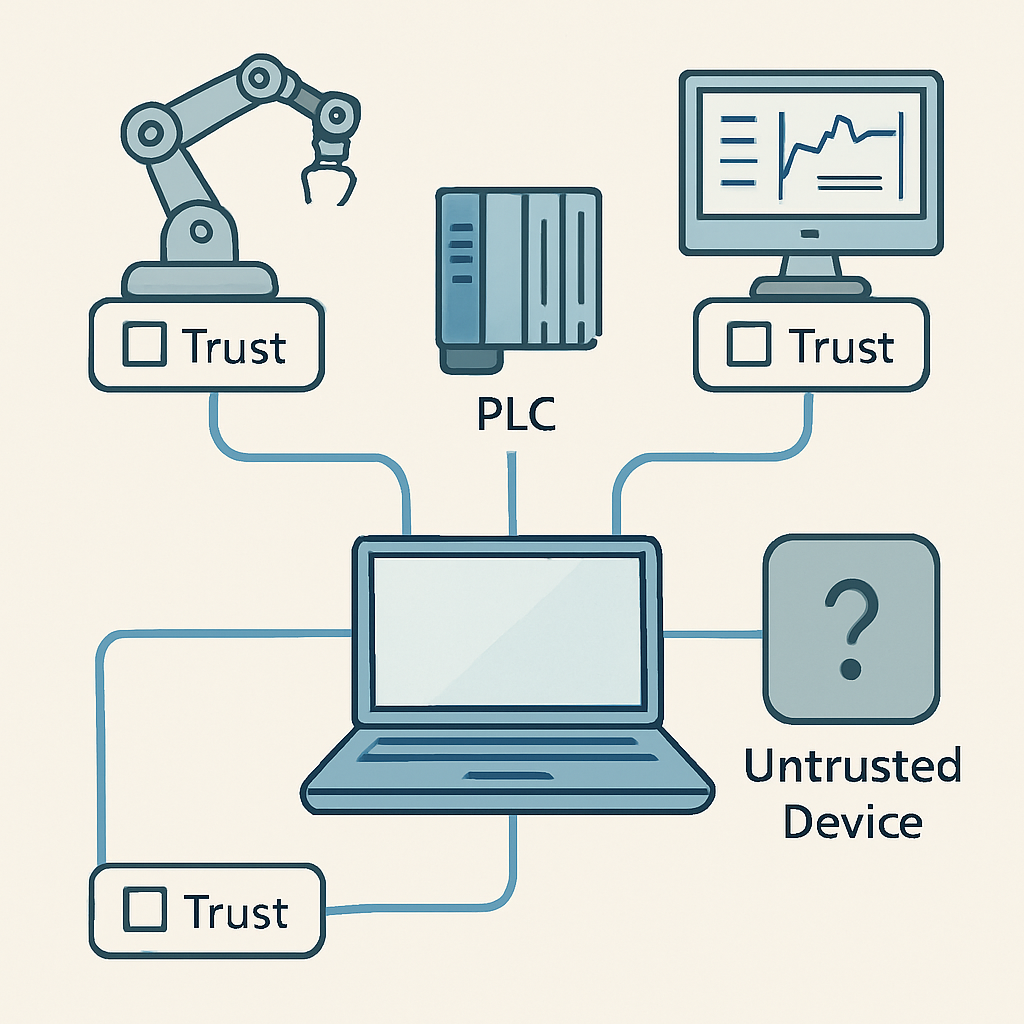
1. Vulnerabilities originating from user accounts and endpoints
The 2025 reports consistently highlight that the first point of compromise is rarely the network itself, but rather user accounts and endpoints. The most frequently exploited areas include:
- Compromised accounts belonging to operators, suppliers, and maintenance staff
- Over-privileged remote access pathways
- Engineering workstations and HMI terminals with weak authentication
- Mobile devices moving between IT and OT environments with little or no verification
- Re-used or duplicated account structures across multiple systems
The reports emphasise that attacks are not succeeding because they are complex, but because unmanaged users, devices, and accounts continue to expand the attack surface.
In other words, the first fracture in OT security does not appear in the network core — it starts at the user and the endpoint.
2. The widening gap between regulatory progress and operational resilience
In 2025, regulatory pressure increased significantly — from the EU NIS2 Directive to updates in international standard IEC 62443, alongside enhanced national frameworks across multiple countries. Yet the reports agree on a shared assessment: while organisations have become far better at preparing documents and ticking compliance checklists, operational resilience on the ground has barely moved.
Key observations include:
- Policies and procedures have become more sophisticated, but the actual response capability of operational teams remains largely unchanged
- RBAC may be defined, yet its consistent application in the field is still lacking
- Incident response playbooks exist, but cross-team coordination remains weak
- Supply chain account and access management continues to be a critical gap, even in regulated environments
- Organisations may pass audits, yet still struggle during real incidents
The overall takeaway: regulatory compliance has improved, but operational resilience has not.
3. The absence of a reliable endpoint-trust model
A recurring theme across the reports is the lack of a robust mechanism to establish trust in endpoints across OT environments.
Common structural issues include:
- Legacy equipment that cannot support stronger authentication
- The continued use of shared or rotating accounts
- OT operations that must continue even during network outages
- Segmented networks that disrupt consistent authentication or log collection
- Engineering workstations becoming single points of failure
Reports frame these not as purely technical limitations, but as structural constraints of OT environments.
Without stable endpoint trust, no defensive layer can be relied upon to function consistently.
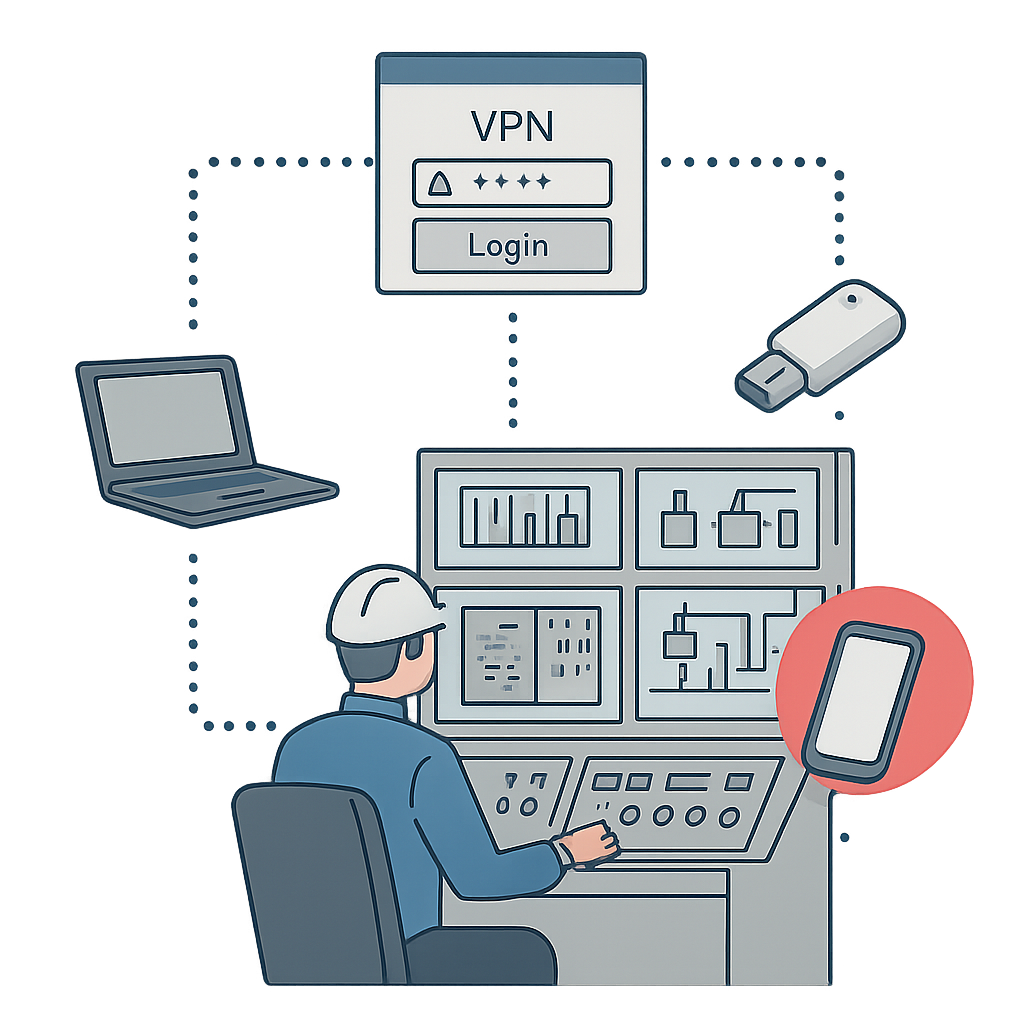
4. Supply chain accounts and access remain the most urgent unresolved risk
Supply chain pathways were one of the most heavily scrutinised weaknesses in the 2025 reports. A significant proportion of initial access attempts originated from supplier accounts and devices.
Key patterns include:
- Stolen VPN credentials from contractors, vendors, and subcontractors
- External devices connecting to operational networks without proper validation
- Maintenance access with unnecessarily broad, or permanently open, permissions
- Fragmented account and access control due to multiple organisations being interconnected
- Complex interdependencies across service providers
Reports describe supply chain account and access management as the longest-standing unresolved issue — and the most clearly exposed structural risk of 2025.
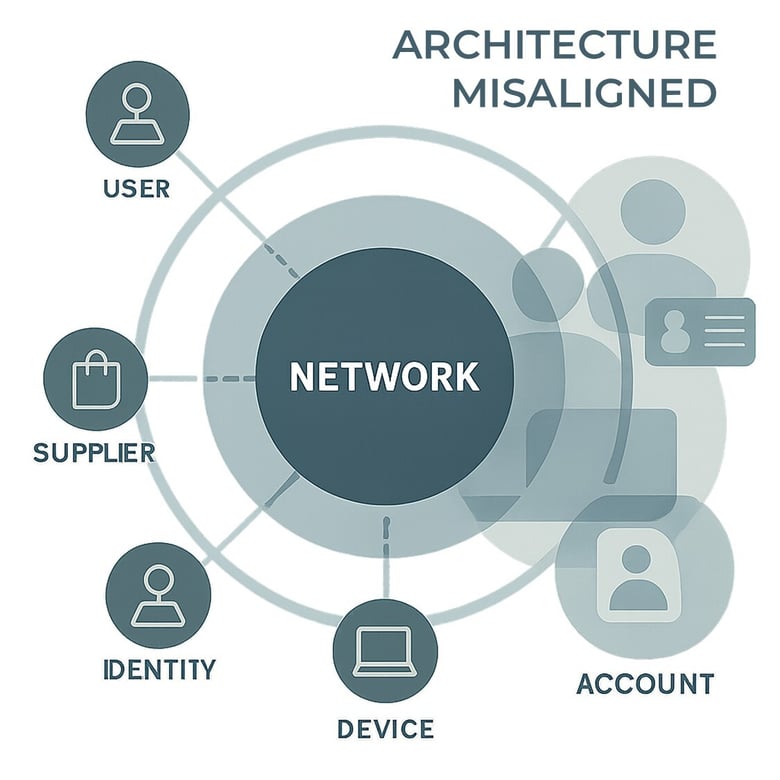
5. A security architecture that still does not place users, accounts, and devices at its centre
Many reports point out that OT security architectures still fail to place users, accounts, and devices at the centre of their design. While policies emphasise their importance, real-world implementation often treats them as add-on controls.
The reports highlight recurring issues such as:
- Principles based on real users and valid accounts being documented, yet inconsistently applied
- Authentication methods built around constant network connectivity — an unrealistic expectation in OT environments
- MFA policies riddled with operational exceptions, undermining overall consistency
- Device and endpoint identity management remaining fragmented across the organisation
- Authentication and access logs dispersed across multiple systems, making unified visibility difficult
The conclusion is clear: unless users, accounts, and devices take a central role in the architecture, structural weaknesses will continue to resurface.
What the reports ultimately tell us
If the incidents of 2025 showed how far attackers reached, the global reports explain why they could do so with such ease.
The recurring message is straightforward: the core weaknesses in OT security lie not in technology, but in operational structures and the way users, devices, and accounts are governed.
And the final conclusion can be summarised in one line:
“The inside of OT may be carefully protected — but the doors leading into it still open far too easily.”
--------------------

swIDch will continue its quest to innovate and pioneer next-generation authentication solutions. To stay up-to-date with the latest trends sign up to our newsletter and check out our latest solutions.

For many OT organisations, Passwordless still feels abstract. The concept is attractive — fewer credentials, fewer

For years, Passwordless has been discussed as a modern authentication approach — faster logins, better user experience,

Industrial operators step into 2026 with clearer mandates, tighter regulations, and rising cyber risk — yet many still
Looking to stay up-to-date with our latest news?