What Makes OTAC Unique
Unlike traditional authentication methods such as ID/password, OTP, SMS, ARS, tokens, and FIDO, OTAC redefines security by eliminating static credentials and network dependencies. While conventional systems rely on stored credentials, repeated authentication requests, or external hardware, OTAC generates a dynamic, one-time authentication code locally—without requiring a network connection.
This means no risk of credential reuse, interception, or phishing. Unlike OTPs and SMS-based methods, which are vulnerable to interception and delays, OTAC ensures seamless, real-time authentication. Unlike FIDO and token-based solutions, which depend on external devices, OTAC is lightweight and scalable, requiring no additional hardware. By enabling both identification and authentication in a single step, OTAC delivers unmatched security, efficiency, and user convenience across industries.
![[JPG] OTAC technology table v2 [JPG] OTAC technology table v2](https://www.swidch.com/hubfs/%5BJPG%5D%20OTAC%20technology%20table%20v2.jpg)
What we offer
swIDch’s OTAC technology combines advantages of the three most common authentication systems – user ID/passwords, RSA hardware/software for generating authentication codes, and tokenisation. This method generates a single dynamic code that both identifies and authenticates the user at the same time and can do so without a network connection. Our one time method cannot be used by anyone else.
Strong & Secure Authentication
OTAC generates dynamic authentication codes—no network required.
Simple & Seamless Integration
API/SDK support ensures easy and frictionless IT admin deployment.
Flexible & Highly Scalable Technology
Lightweight OTAC applies across industries, beyond just devices.
Cost-Saving & Hassle-Free Security
Cut token infrastructure. Reduce traffic, maintenance, and fraud costs.
How OTAC works
Build customisable, flexible solutions depending on your industry and use case. The generation of the code can happen locally on the device or even on the IC chip across a range of cards and applications. The format is then configurable to each client's needs, along with the transfer and verification.
This flexibility combined with configurable time intervals provides a highly flexible and super secure authentication solution across a wide range of industries, and unique to every client's needs and requirements.

350 Patents Filed • 210 Granted







Award Highlights

Contact us today
OTAC FAQs
-
OTAC stands for one time authentication code.
-
Static credentials such as card numbers, IDs, passwords, and PINs remain unchanged over time, making them vulnerable to theft and misuse. Cybercriminals can exploit these credentials through identity theft, card-not-present fraud, and account hijacking. Additionally, maintaining knowledge-based authentication systems is costly and burdensome for both users and organisations.
-
OTP (One-Time Password) cannot independently verify a user’s identity. It always requires an initial authentication step, typically a username and password. This multi-step process increases complexity for users while still relying on static credentials for the initial login, leaving vulnerabilities open to exploitation.
-
Many authentication methods, such as tokens, depend on a network connection to validate user access. In areas with limited connectivity, authentication can become unreliable or even impossible. Token-based authentication also requires a connection between a user, a server, and a third-party service provider (TSP), restricting its use to controlled network environments.
-
OTAC eliminates the need for static credentials, reducing the risk of theft and fraud. Unlike OTPs, it performs both identification and authentication in a single step, streamlining the user experience. Additionally, OTAC operates without requiring a network connection, making it highly effective in offline or low-connectivity environments.
-
Yes, OTAC doesn’t require network connections or phone signal to work.
Why swIDch
that provides all of the following features, tested and substantiated
by the University of Surrey technical report
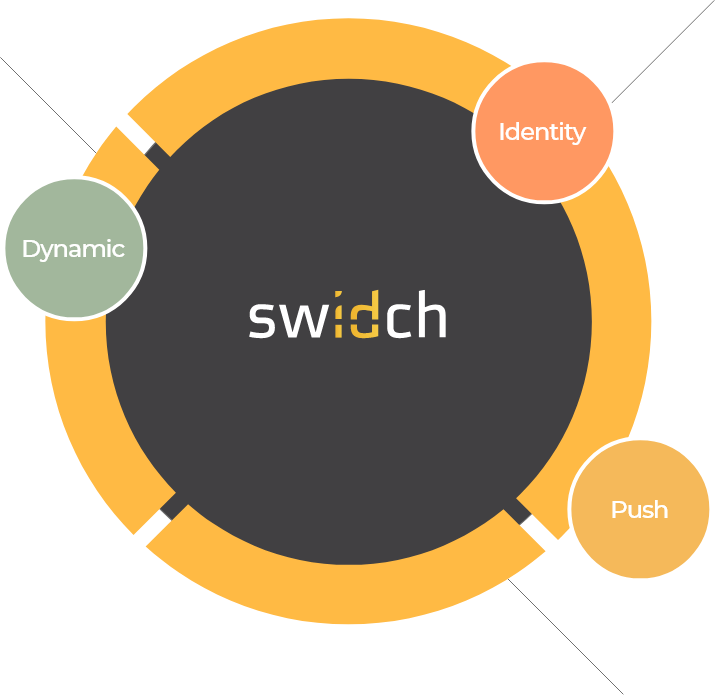
sufficient to IDENTIFY user
and AUTHENTICATION
off-the-network environment
Single-step identification and authentication with the code alone. Include our biometric option and get single-step MFA. Vastly improved UX by removing steps.
OTAC is a dynamic code, which means the code is constantly changing. Eliminates all use of static information. Forget usernames and passwords forever. Vastly reduced workload for IT helpdesks.
No network connection required for generating OTAC, enabling uninterrupted use no matter where you are. No more waiting for additional tokens/OTPs and no need for heavy public key infrastructure (PKI).
Highly configurable code parameters and lightweight SDK/applet means wide range of deployment options on many devices across multiple sectors.










.jpg)