

M2M
fraud prevention and identity proofing.
Pain points
In the IoT era, Machine-to-Machine communication technology is the key to establishing an industrial automation environment through information exchange between various devices such as sensors and gateways. Therefore, maintaining a strong authentication network is the first step for a smart factory infrastructure.


Replay attack
Replay attack
In the process of verifying that the user is correct, the server system exchanges encrypted data such as electronic signatures between users. In the meantime, a third-party hacker tries to impersonate a legitimate user by copying
the data that is in transit on the network and then transmitting it to the server as it is.
For example, if an industrial robot that performs a service based on recorded data is subjected to a replay attack,
it may not be able to perform normal tasks and may endanger workers nearby.


Impersonation attack
Impersonation attack
In a modern factory system, numerous machines are paired and operated for efficient production.
An impersonation attack is tricked into being a device connected to each other using a persistent encryption key
or a long-term key used when multiple devices are first paired. Since the mutual authentication process is no
longer required, the attacker controls the devices as the master.
The solution
swIDch helps manufacturing companies in the industry 4.0 era complete a successful digital
transformation by providing a more secure authentication process to each device and user that make up the manufacturing system.
- Provide unidirectional code generated by the client without communication with the server
- Generate a dynamic code that is changed every time and is safe from hacking and leakage
- Block attacks in advance with one-time code that does not allow cloning and spoofing attacks
- Protect devices by issuing a unique code that never overlaps with other connected devices
OTAC in M2M
Machine to Machine (M2M) Authentication
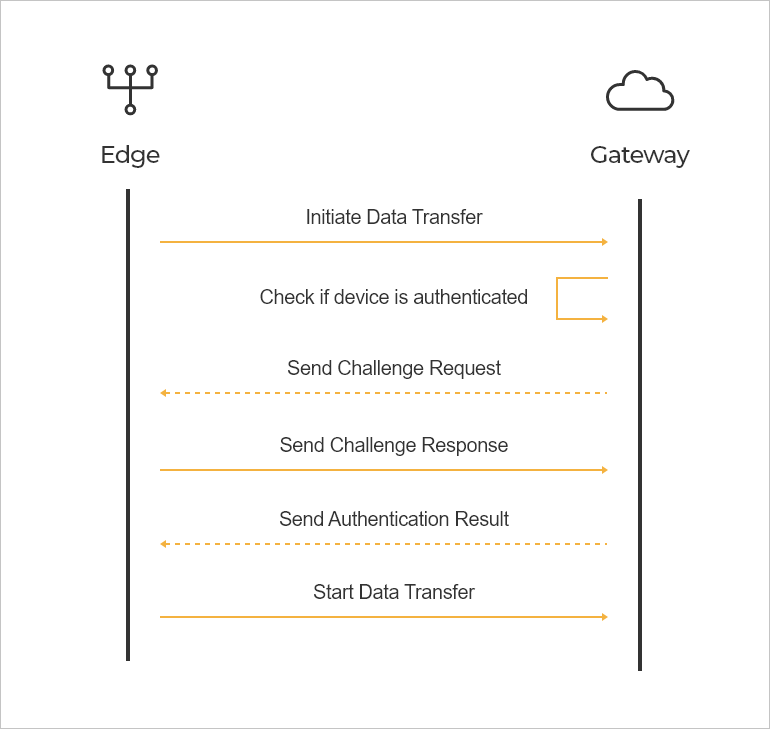
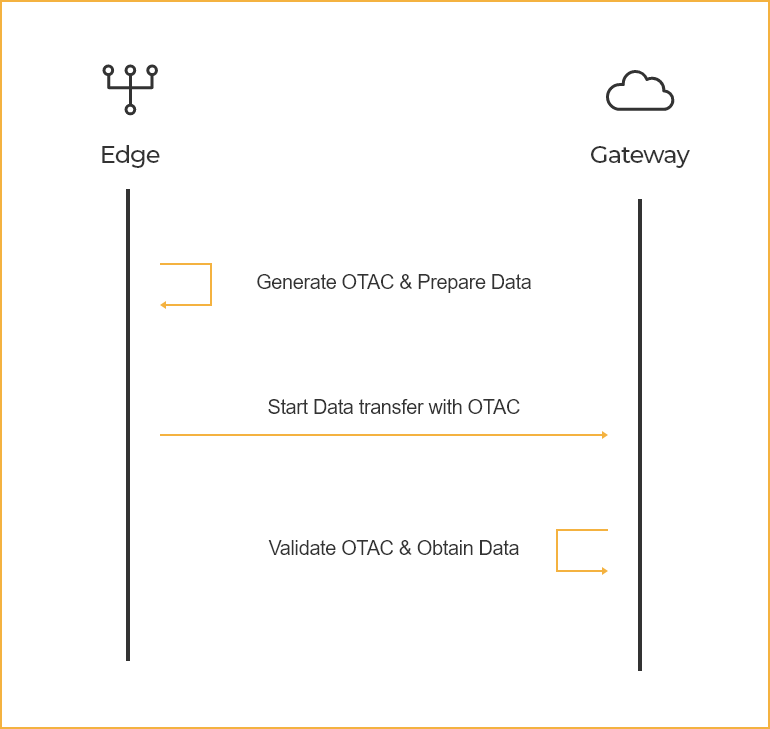

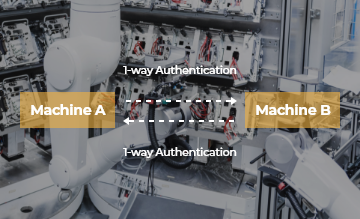
Machines and Robots in a factory that are talking to each other directly with OTAC
to coordinate production activities.
swIDch’s core algorithm allows secure authentication of a user in a single ended flow, greatly reducing the number of round trips in M2M communication.
However, it can also be adapted to authorise a role: to determine what an authenticated user is allowed to do. When a user authenticates using OTAC,
the authentication server can return a second OTAC containing information about that user’s role and a digital signature authorizing that user to access permitted resources.
The user’s OTAC and the authorisation OTAC can then be combined into a passport OTAC,
which can be used by a service requiring access to another service’s resources as a dynamic guarantee of authorisation.
This second service can then interpret the passport OTAC, only granting access where the original user’s role authorises it.
All the information the called service needs is encapsulated securely and dynamically in the passport OTAC, assuring trust without the need for an external service.
Only swIDch’s proprietary technology can support this form of distributed authorisation, giving our customers a world-beating,
performance-oriented solution to the vital problem of trust. We consider this distributed authorisation the future of trust in large service networks!
Why swIDch
that provides all of the following features, tested and substantiated
by the University of Surrey technical report
Sufficient to IDENTIFY user
that does NOT duplicate
in off-the-network environment
OTAC is a dynamic code, which means the code keeps changing. As a result, you don’t need to worry about any leak of your personal information, such as
your card details, because the codes must have already been changed when others try to use them.
The network connection is NOT necessary at all for generating OTAC.
Reducing an authentication stage that requires the network connection directly means there are fewer gateways for
the hackers to access our personal information.
Moreover, this feature enables users
to authenticate even when they are
in networkless environments, such
as on the plane, underground, rural or foreign areas.
swIDch can guarantee that the code never duplicates with anyone
at any given moment.
There is NO chance of someone else having the same code.
The users or their devices can be identified with the code alone.
Once OTAC has been generated, providing OTAC alone is already fully sufficient to identify the user as the code is unique.
It means, you can forget about the bundles of static information including IDs and passwords.