Is 2021 the 'last hurrah' for passwords?

Last year the Covid-19 pandemic saw a radical shift to remote working for many industries. Organisations across the globe were forced to develop new strategies to manage daily tasks and accomplish future goals proficiently and in a cost-effective manner. One aspect which did not change however was the problems posed by passwords.
The merging of home and office work has resulted in a merging of home and office security. Networks we use and manage ourselves are often times less secure due to lack of stringent best practices than those imposed by a business or an organisation. In addition to this, staff are more likely to be accessing systems at unusual times (out-of-hours) and access systems regularly that didn’t need regular access previously. The risk posed by a less secure network introducing a threat to a business network has grown exponentially. These factors combine to produce a greatly expanded attack surface for hackers to exploit. As a result, cybercriminals and hackers have increased their efforts in targeting this new ‘work from home’ group in the hope of infiltrating an entire network or business system, where the rewards (and damage) can be far reaching. Some key stats below:
- Cybercrime costing global economy $2.9m every minute
- 1 in 250 corporate accounts compromised each month
- 80% data breaches occur due to poor passwords
- 65% of people continue to reuse the same password for multiple online accounts
- 20-50% of all help desk calls were regarding password resets
Static passwords are a huge contributing factor to these stats. They excel in contributing to user aggravation (who hasn’t forgotten a password at some point?), one small mistake upon manual entry can lead to a whole world of pain including lock outs and password resets. It often comes down to human nature. It is a huge inconvenience to try and come up with entirely new ‘complex’ passwords and then to try and remember them across multiple platforms. Nonetheless, it is these factors which continue to motivate cybercriminals to attack. The main vulnerability of passwords is due to the fact they are formulated by static information and there are multiple ways hackers exploit this.
What are the most common forms of attack for hackers?
Phishing is one of the most well-known and widely known attack methods. Most common techniques are via email and text (sms), but they are not limited to these sources. The trick is to get the user to click on and hopefully interact with a malicious source, presented as being wholly trustworthy. As people have become more aware of these attacks, techniques have become more sophisticated, implementing social engineering where the content appears to come from a well known organization or person. This can pose a huge problem for business and enterprise when hackers impersonate senior level executives asking employees themselves for information.
‘Brute forcing’ uses excessive forceful attempts via trial-and-error to guess login information and ‘force’ their way into accounts. There are many different types of brute force attacks. It is an old attack method but is still widely used. The time it takes for this method to be successful depends on the complexity of the passwords they are trying to crack. One of the most common forms, a ‘Dictionary attack’ (a type of brute forcing attack), attempts to gain illegal access to personal information by using a very large set of words (often using a dictionary – hence the name) to generate potential passwords. Hackers will often use software to speed up this process removing the need for manual input, but the attempted combinations required before a password is hacked often remains vast.

Business attempts to enhance password security often falls flat
Password re-use, where users use the same password across multiple accounts is also a common problem and a tactic nearly all attackers will attempt to exploit if an initial password is cracked.
To increase security many businesses opt for mandatory password reset schedules such as monthly, bi-monthly or quarterly. However, when staff are forced into change, they often revert to predictable behavioral patterns to avoid password locks outs and aid their ability to recall the passwords going forward. This approach from business is somewhat counter-intuitive due to the fact it overlooks the vulnerability of a particular password itself and instead focuses on regular resets. If a password has not been hacked there is no need to reset it, and if a password has been hacked then resetting with only a slight variation does not solve the overriding vulnerability issue.
Previous advice has focused on ensuring passwords themselves are complex. One tactic users commonly use it replace numbers with letters for example ‘L0nd0n’ with zeros. The problem is attackers quickly gain knowledge of these tactics and use it to enhance their attacks and according to CNET, they do not make that much difference to password strength. More important is the length of the password, but this in itself poses additional problems for the user in remembering the passwords in the future.
A Which magazine report from October 2020 highlighted stolen accounts and data (including passwords) were being openly sold of the dark web for profit. Companies whose data was for sale included UK supermarket giant Tesco, Deliveroo & McDonalds (amongst others). The knock-on effect of data breaches of this sort for business and the consumer cannot be underestimated, and these often stem from vulnerable security protocols, particularly static passwords.
The new GDPR Regulation in Europe in 2018 set strict rules regarding the protection of personal data imposing strict fines for breaches in an attempt to motivate companies to enhance their data security practices (including passwords). However, the input of each individual implementing these practices still remains paramount and thus provides the greatest vulnerability due to the lack of employee conformity.
Microsoft, has long proposed an end to passwords, naming 2020 ‘a banner year for passwordless technology’ with an aim this year ‘to make passwordless access a reality for all our customers in 2021’ in a recent blog post. Multi-factor authentication (MFA) is one of the most effective ways to provide additional protection to a password-protected account. According to Microsoft, accounts are more than 99.9% less likely to be compromised if MFA is enabled. This does beg the question as to why have passwords in the first place if we are only trying to counteract its weakness via MFA? This is a thought echoed in a 2020 report released by the World Economic Forum which stated that freeing ourselves of passwords will make us safer and businesses more efficient.
We agree, which is why our own OTAC technology does away with passwords all-together. Static information from password logins poses a vast array of problems for businesses and consumers. The revolution is coming. Make sure you and your business are on board.
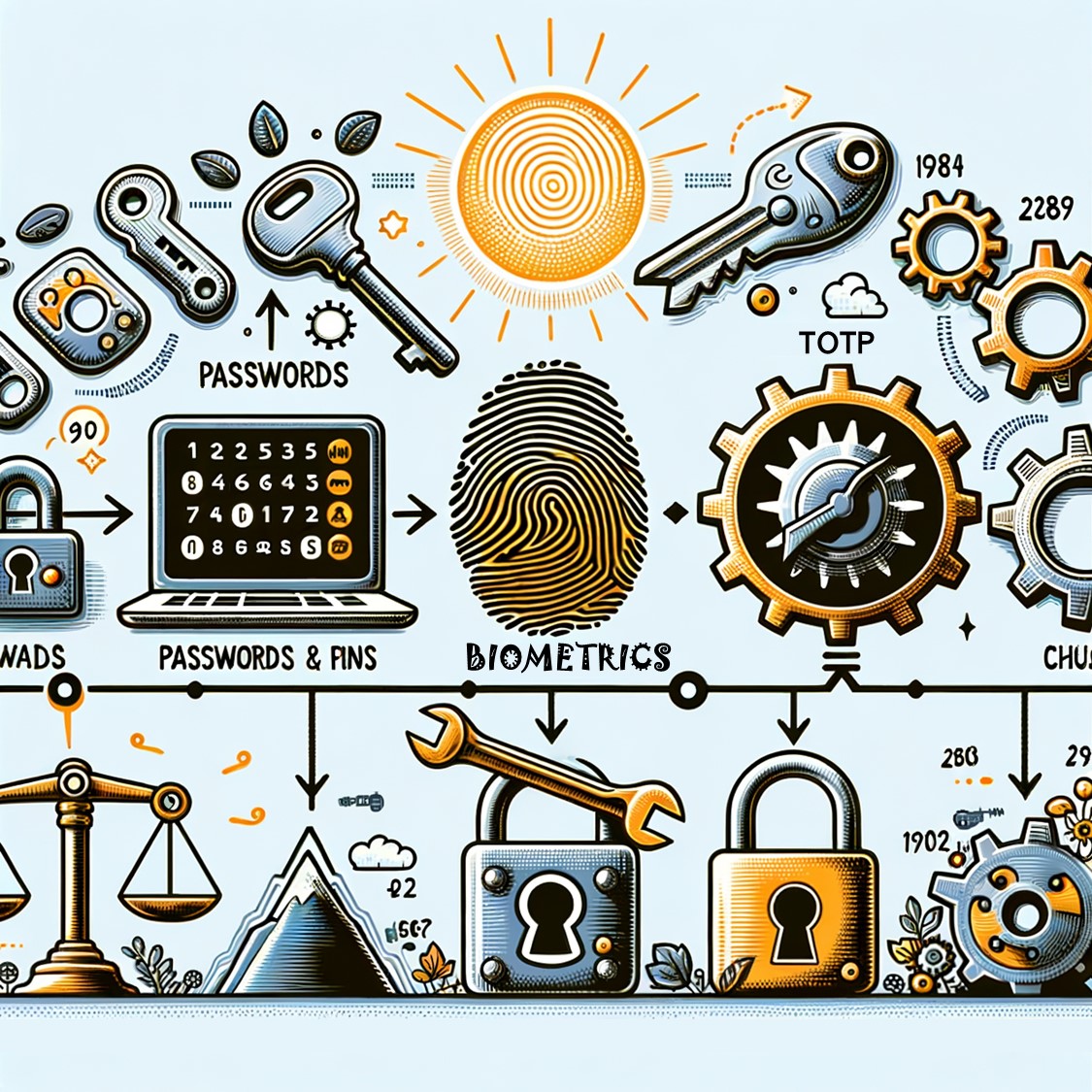
In the dynamic landscape of cybersecurity, authentication serves as a crucial barrier against unauthorized access and

Quantum computers represent a paradigm shift in computation, leveraging the unique properties of quantum mechanics to

In recent headlines, an Israel-linked group has claimed responsibility for a cyberattack that disrupted operations at
Looking to stay up-to-date with our latest news?